Intrusion Analysis Reveals Overlap in RansomHub, DragonForce, and Play Ransomware Operations
- Threat actors overlap: Security researchers discovered traces of operational overlaps between DragonForce, RansomHub, and Play ransomware.
- Initial access: A recently discovered campaign used a fake DeskSoft’s EarthTime application that disseminated SectopRAT malware.
- Gang-specific tools: It featured a Play-specific reconnaissance tool, a NetScan output linked to DragonForce, and the RansomHub-correlated backdoor.
Significant Play, RansomHub, and DragonForce Ransomware operational overlaps were seen in a sophisticated attack that utilized tools and tactics associated with each gang, highlighting a potential affiliate operating across multiple ransomware-as-a-service (RaaS) platforms and blurring the lines in the cybersecurity threat landscape.
Attack Chain and Shared Tooling
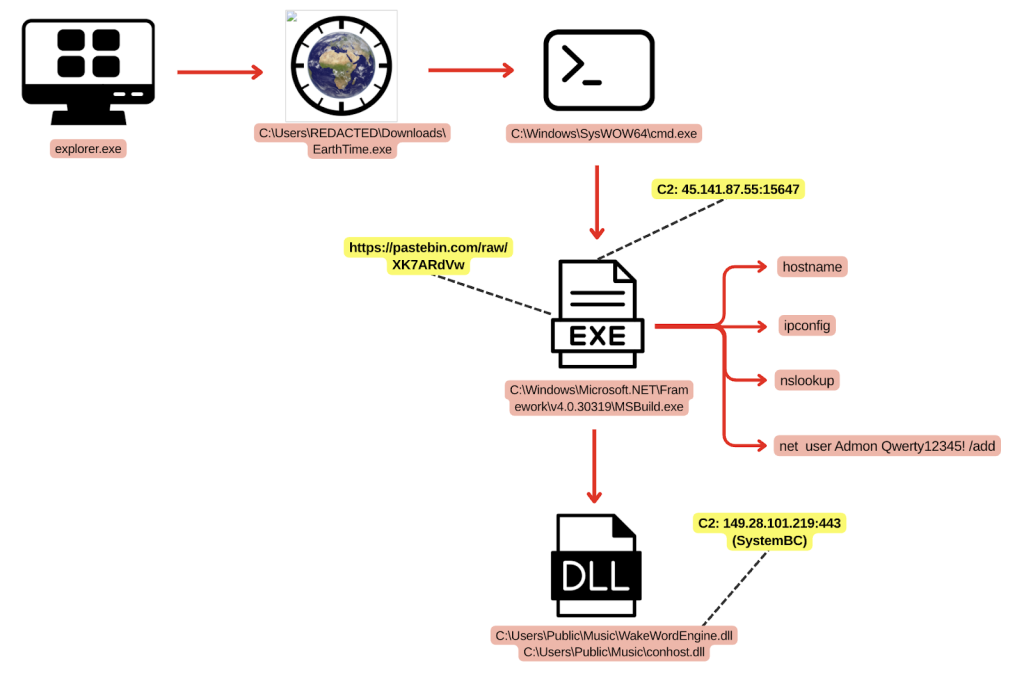
The intrusion began when a user executed a malicious file masquerading as a legitimate EarthTime application, which deployed SectopRAT, a .NET-based remote access trojan (RAT) with information-stealing capabilities, according to a recent intrusion analysis published by The DFIR Report.
The threat actor then used SystemBC for proxy tunneling and later deployed the Betruger backdoor, a tool linked to RansomHub affiliates. Throughout the attack, the actor performed lateral movement using Remote Desktop Protocol (RDP) and Impacket's wmiexec and leveraged Microsoft Sysinternals’ PsExec utility for local privilege escalation.
Crucially, the analysis identified the use of Grixba, a custom reconnaissance tool exclusively associated with Play ransomware tools.
Further investigation revealed operational security failures by the attacker, who left behind a network scan output file containing data from a company previously compromised by DragonForce ransomware.
This evidence strongly suggests the threat actor may be an affiliate working with multiple ransomware syndicates. A March report underlined RansomHub links to Play, Medusa, and BianLian Ransomware via shared EDRKillShifter use. However, DragonForce ransomware claimed expansion amid an alleged RansomHub takeover in April.
Cybersecurity Implications
This case demonstrates the fluid and interconnected nature of the modern cybercriminal ecosystem. Affiliates are not necessarily loyal to a single RaaS provider and can leverage a diverse arsenal of tools and malware, including SectopRAT, SystemBC, and Betruger, to achieve their objectives.
This blending of TTPs makes attribution more complex and complicates defensive strategies. The findings underscore the need for comprehensive threat intelligence and robust detection capabilities to identify shared indicators and defend against an evolving and collaborative adversary.
In January, TechNadu reported that cybercriminals leveraged GitHub for distributing Lumma Stealer, Vidar Stealer, SectopRAT, and Cobeacon. SystemBC was also distributed in a data theft campaign using fake IT calls and AnyDesk in 2024.