FIFA World Cup 2026 Scams Emerge as Threat Actors Register Hundreds of Malicious Domains
- World Cup scams: Malicious, FIFA-themed domain registrations leverage typosquatting and brand impersonation to deceive unsuspecting victims.
- Fake domains: These sites are often registered well in advance to establish a history of legitimacy.
- Who is targeted: Scammers aim these sites at fans, sponsors, and businesses associated with the global tournament.
A significant surge in malicious domain registrations was observed that contain FIFA, football (soccer), and World Cup-related brand terms. This activity signals a large-scale effort by cybercriminals to launch numerous FIFA World Cup 2026 scams targeting fans, sponsors, and businesses associated with the global tournament in anticipation of the event.
Proactive Threat Actor Tactics
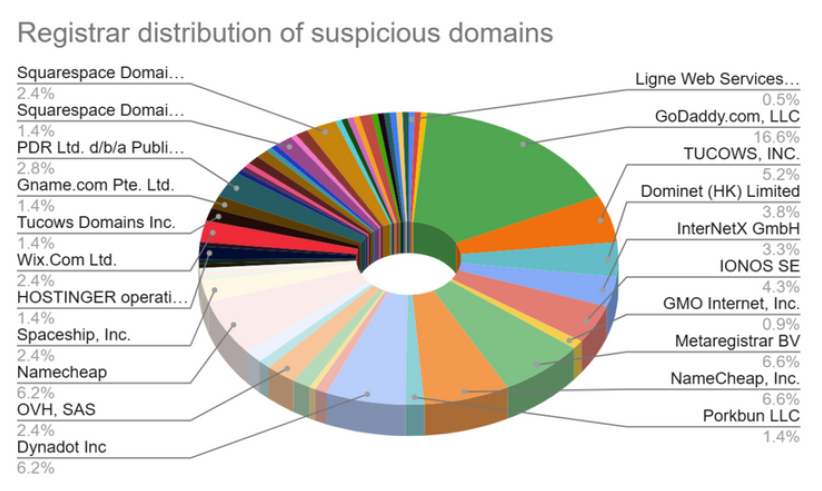
Analysis of 498 suspicious domains, with 173 domains using “FIFA” and 129 using “worldcup,” reveals that threat actors are employing long-term strategies to evade detection, according to a recent threat intelligence report from BforeAI's PreCrime Labs.
The report shows the following Top-Level Domain (TLD) distribution:
- .com = 300 (58.9%)
- .online = 36 (7.1%)
- .football = 24 (4.7%)
- .org = 14 (2.8%)
- .xyz and .shop = 13 each (2.6%)
Among the 498 domains, .com dominated with nearly 59%, followed by .online, .football, .org, .xyz, and .shop, reflecting the use of thematic TLDs.
Exhibiting multiple red-flag clusters commonly used in scams and phishing around major sporting events (including 2024 and 2025), these domains involve obvious trademark typosquats, speculative registrations, generic fan/merchandise/betting names, and community or amateur football sites.
Many suspicious FIFA websites were registered well in advance, with some domains already secured for the 2030 and 2034 tournaments. This "domain aging" tactic is designed to establish a history of legitimacy, enabling sites to bypass security filters more effectively as the event approaches.
BforeAI on the FIFA World Cup Scam
Expert comments from Rishika Desai, Threat Researcher and Writer at BforeAI shared with us suggest that this operation does not appear to be heavily automated, despite company data indicating a significant spike in registrations between August 8 and August 12, 2025.
Over that period, 299 domains were registered, with an average of 53 per day, and registrars such as GoDaddy and Namecheap experienced heavy utilization.
“We also observed an AI-generated domain pattern as a batch, in one specific case, 11 domains, suggesting algorithmic usage,” Desai said, adding that the pattern followed the structure fifacwc-[xx]-shijubei[.]com with dynamically-created central characters.
Desai also highlighted the geographic spread of these registrations. The majority originated from the United States (72), followed by China (37), with smaller but noteworthy clusters in Iceland (20), Canada (17), and the Netherlands (14).
This mix reflects both high-volume U.S. registrar usage and offshore privacy-friendly hubs, reinforcing the global nature of the threat infrastructure.
Types of Fraudulent Schemes
The report identifies several high-risk fraud categories being prepared. The most common themes include counterfeit merchandise stores, fraudulent ticket sales portals, and illegal streaming websites designed to harvest credentials or distribute malware.
Additionally, domains are targeting host cities like Dallas and Atlanta with travel-related lures, including fake hotel and visa services. Other schemes involve betting platforms and cryptocurrency scams, such as fraudulent "FIFA Coin" initial coin offerings (ICOs) via ETH with a static cryptocurrency wallet address.
Top themes exploited are:
- 56 World Cup or team merchandise (shops or stores selling scarves, jerseys, etc.)
- 55 streaming and live access to watch the matches
- 32 betting (slot and casino)
- 2 ticketing for live matches
- 23 targeting host cities (Dallas, Atlanta, Kansas City, Philadelphia, Texas)
- 2 using account/auth terms like “login” or “register”
- 3 spoofing Visa or hotels
- 1 related to VPN
FIFA Scam Awareness Is Recommended
This proactive infrastructure setup highlights the evolving landscape of cybersecurity for global events, requiring heightened vigilance from both organizations and individuals to mitigate the risks of financial loss and data theft.
In other news, scammers recently registered over 70 suspicious domains with a Texas flood disaster relief theme, and at least 70 individuals reported being tricked in Labubu toy scams.