Wallarm Q2 2025 Report: APIs Confirmed as Primary Attack Vector
- Threat trends: API vulnerabilities and AI-related risks are rising, with over 600 API-related CVEs disclosed in Q2 2025.
- Strategic shift: Threat actors move towards exploiting misconfigurations and business logic flaws on top of flaw exploits.
- In numbers: Cybersecurity researchers say the second quarter of 2025 saw a 9.8% increase in API-related CVEs compared to Q1.
A significant escalation in API-centric cyber threats confirms that Application Programming Interfaces (APIs) are the primary attack vector for modern enterprises, with threat actors increasingly exploiting misconfigurations and business logic flaws rather than relying solely on traditional vulnerabilities.
The comprehensive API breach analysis is detailed in the report called Q2 2025 API ThreatStats Report from Wallarm, a unified platform for API and agentic AI security deployed in enterprise production environments.
Key API Security Trends 2025
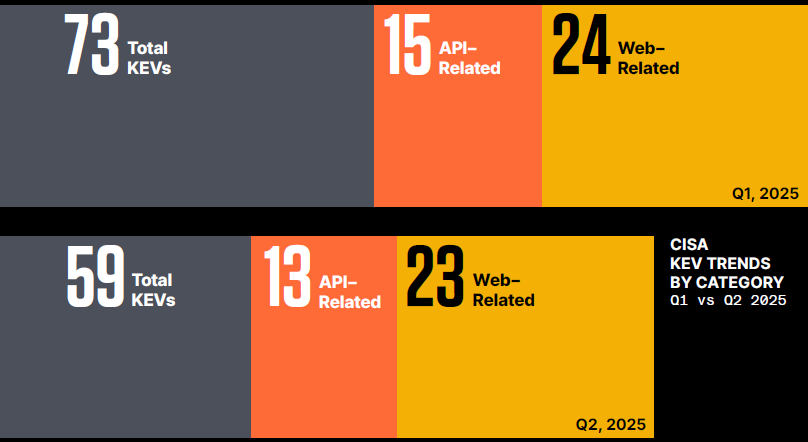
According to the report, the second quarter of 2025 saw a 9.8% increase in API-related CVEs compared to Q1, with 639 unique vulnerabilities disclosed. A notable trend is the acceleration of AI-specific API vulnerabilities, which nearly doubled from 19 in Q1 to 34 in Q2.
These flaws primarily impact AI model-serving endpoints and orchestration frameworks, highlighting the convergence of API and AI security risks.
Analysis of the CISA Known Exploited Vulnerabilities (KEV) catalog reveals that API-related exploits accounted for 22% of all 59 confirmed in-the-wild attacks for the quarter.
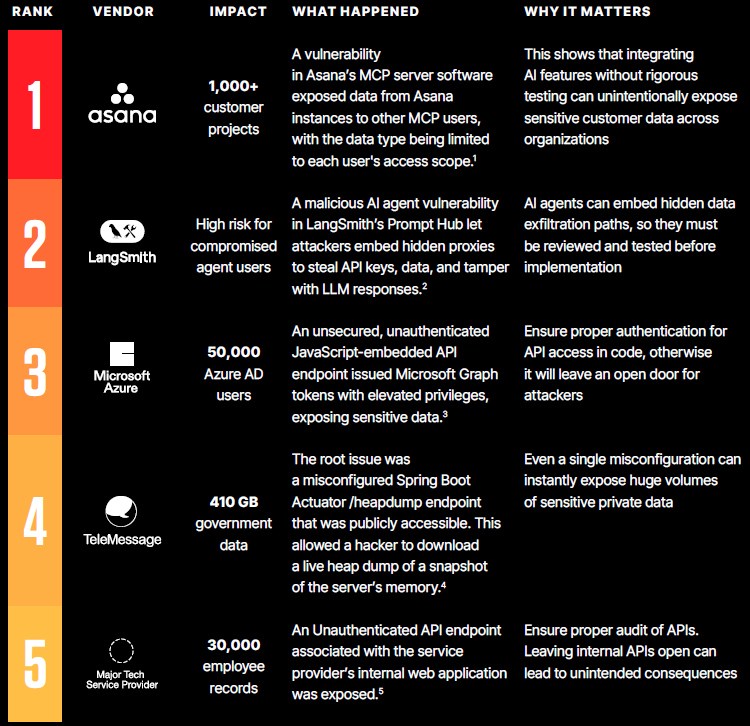
Common exploitation themes included unauthenticated access points, Broken Object Level Authorization (BOLA), token abuse, and injection and execution flaws. High-profile breaches at companies like Asana, Microsoft Azure, and LangSmith stemmed from these fundamental security oversights.
“Attackers are no longer just scanning for outdated libraries; they're exploiting the way APIs behave, especially those powering AI systems and automation,” said Ivan Novikov, CEO and Co-founder of Wallarm. “Security teams must expand their visibility to include runtime context and adopt testing approaches that match the complexity of today’s dynamic, interconnected APIs.”
Wallarm's Security Strategist Tim Erlin told TechNadu that effective vulnerability detection and attack prevention require a deep understanding of application logic—something that, for now, still relies heavily on human expertise.
“Of course, finding vulnerabilities is important, but so is detecting attacks as they happen. They're two sides of the same coin, and both require that understanding of the normal application logic,” he added.
Erlin also warns that development environments, often assumed to be internal and thus less protected, now face heightened risk due to the increasing integration of cloud, SaaS, and external partners.
“Most organizations are still in the process of recognizing that their perimeter doesn’t really exist any longer,” he said. He added that “internal tools are often accessible externally or through other external tools,” which makes them just as exposed as production systems.
As such, Erin stresses these environments must be secured to the same standard as any external-facing production service.
Recommendations from the Report
The Wallarm API ThreatStats Report underscores that attackers are leveraging legitimate API functionality to orchestrate breaches. Major incidents in Q2 often required little more than sending an HTTP request to an exposed or improperly secured endpoint.
To counter these evolving threats, the report issues several key imperatives for security leaders.
- Establish full API visibility
- Secure the AI stack
- Harden authorization and authentication
- Move beyond schema checks and test for logic flaws
- Combine API security testing with inline runtime protection