Six Months On: Manpower Confirms Data Breach After RansomHub’s December–January Access
- Attack confirmation: Manpower confirms a breach impacting over 144,000 individuals in the United States.
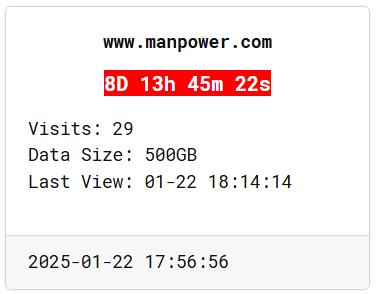
- January 2025: RansomHub claimed the Manpower breach, alleging theft of 500 GB of data.
- Month-long access: Attackers accessed its systems between December 2024 and January 2025
After six months of a ransomware group claiming responsibility for the Manpower data breach, the staffing giant Manpower confirmed it had suffered a data breach. The official statement by the leading staffing firm publicly disclosed the incident this month.
Details about the Manpower Data Breach
A Claim Depot notification stated that an IT outage was experienced by Manpower’s Lansing office on January 20, 2025. The incident impacted access to systems.
Two days later, the RansomHub group made a dark web announcement claiming it had breached Manpower and exfiltrated 500GB of data. They also gave a deadline of 8 days for ransom payment.
“The companies' investigations revealed that a hacker had gained unauthorized access to the company’s network between December 29, 2024, and January 12, 2025,” the Claim Depot report added.
During that time, personal information such as names, Social Security numbers, driver’s licenses, government-issued IDs, including passports and state ID cards, and medical data was stolen by the hackers, according to investigators.
The stolen data affected 144,189 individuals in the United States. This included 588 individuals in Texas, 11 in Maine, and 35 in Massachusetts.
Targeting Manpower for Employee Data
Impersonation and identity theft are common tactics used to compromise large enterprises. For example, in the recent vendor breach of Air France and KLM, attackers gained access by targeting a third-party customer service platform.
The attackers obtained names, contact details, and loyalty data and later used those fragments for phishing and identity-targeted attacks.
ManpowerGroup is one of the world’s largest workforce solutions companies, serving over 600,000 individuals and operating in more than 70 countries. Because it connects millions of workers with businesses across industries, it makes it a rich target for attackers seeking personal and corporate data.
This stolen data could be resold on the dark web markets for creating duplicate identity documents and duping organizations.