Four Zero-Click DoS Flaws Abuse Windows RPC and LDAP to Launch Large-Scale DDoS via Domain Controllers
- RPC abuse: Exploiting flaws in Microsoft Windows’ Remote Procedure Call revealed four new DoS vulnerabilities.
- New attack: Researchers claim to have developed a novel DDoS attack that leverages public domain controllers to create a malicious botnet.
- Technique: The innovation lies in using legitimate system components to bypass conventional defenses.
A series of newly identified, now-patched DDoS vulnerabilities exploit blind spots in Microsoft's Windows Remote Procedure Call (RPC) and LDAP protocols to orchestrate advanced denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks, highlighting the growing risk of RPC abuse.
Novel Attack Techniques
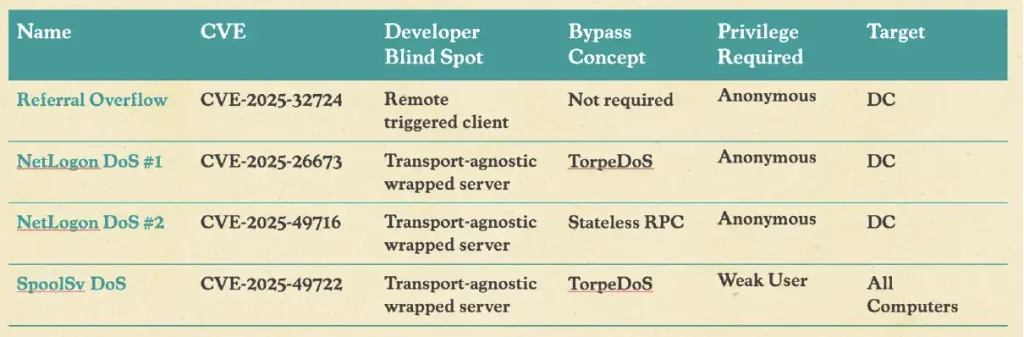
A SafeBreach research uncovered four critical DoS vulnerabilities, including CVE-2025-32724 and CVE-2025-26673, which exploit blind spots in Windows domain controllers (DCs) and Active Directory systems.
Three new DoS flaws allow crashing DCs without authentication, and one new DoS vulnerability enables any authenticated user to crash any DC or Windows computer in a domain.
By manipulating components such as the LDAP client and RPC server code, attackers can cause severe service disruptions through resource exhaustion. A particularly disruptive technique, termed Win-DDoS, leverages public domain controllers as an untraceable botnet.
Attackers trick these systems into sending thousands of referral requests to a single server, overwhelming its resources and enabling large-scale DDoS attacks without leaving a footprint.
The innovation lies in using legitimate system components to orchestrate these attacks, bypassing conventional defenses.
A demo is available, showing how Win-DDoS is executed to recruit three DCs and flood a dummy server.
Implications for Cybersecurity
The vulnerabilities, described as zero-click and requiring minimal privileges to exploit, challenge foundational assumptions about enterprise network security. Systems previously deemed safe from DoS threats, such as private domain controllers, are now vulnerable.
This expands the attack surface for threat actors, with potential ramifications including halted organizational operations, crippled infrastructures, and significant financial losses.
SafeBreach emphasized the broader significance of addressing these weaknesses, noting that resource exhaustion exploits could also frame governments or enterprises for cyberattacks, adding layers of geopolitical complexity to these cybersecurity threats.
Defensive Measures
SafeBreach responsibly disclosed these findings via their original analysis to Microsoft, which has since patched the vulnerabilities.
To mitigate similar risks, organizations are urged to adopt robust threat modeling, strengthen internal network defenses, and enforce real-time monitoring capabilities. By addressing these systemic vulnerabilities, businesses can better prepare for the growing sophistication of DoS attacks.
This year, Cloudflare reported the largest, 5.6 Tbps Mirai DDoS attack.