macOS.ZuRu Malware Resurges via Modified Khepri C2 and Trojanized Termius App
- The macOS.ZuRu malware resurfaced, hiding in the popular SSH client and server-management Termius app.
- The novel variant uses the open-source Khepri C2 framework with severe consequences.
- Infection can lead to unauthorized data access, operational disruption, and potential espionage.
The notorious macOS.ZuRu malware has re-emerged, exploiting advanced techniques to attack macOS users. The latest variant utilizes the open-source Khepri C2 framework and disguises itself within a compromised version of the Termius app, a popular SSH client and server-management tool.
Heath Renfrow, Chief Information Security Officer and Co-founder at Fenix24, stressed that the core issue is social engineering, not a novel vulnerability in macOS.
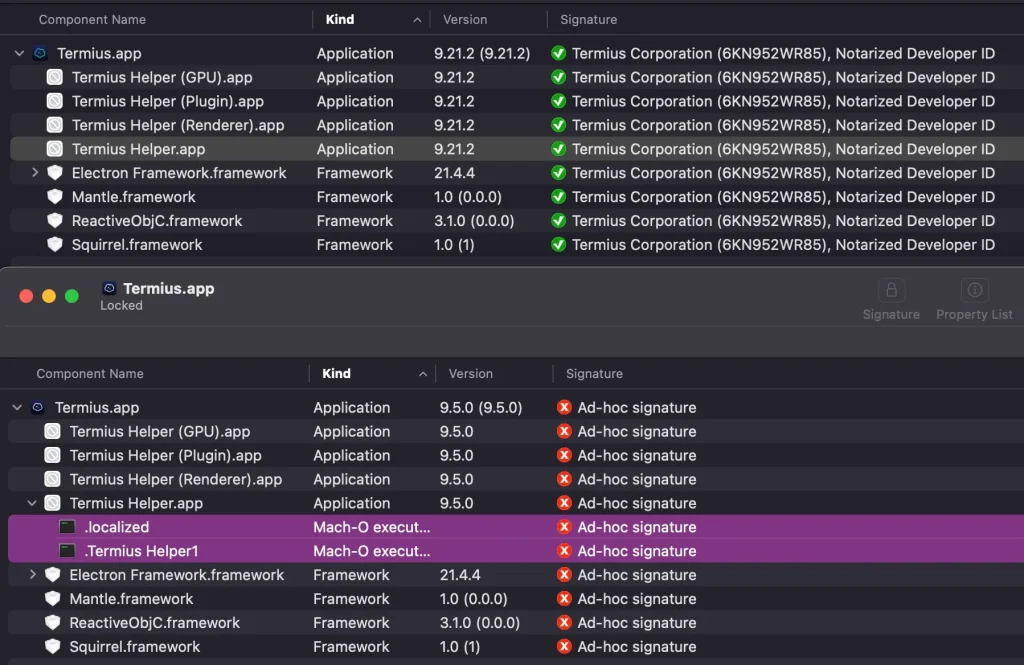
Delivered through a malicious .dmg disk image, the altered Termius app is repackaged with harmful binaries, inflating its usual size from 225MB to 248MB. Once installed, the application executes modified helpers and loaders that function as carriers of malware.
A comprehensive SentinelOne report said the malicious component .localized downloads additional payloads from a remote Command-and-Control (C2) server at download.termius[.]info and stores them in hidden system directories, such as /tmp/.fseventsd.
The core payload—a customized Mach-O binary—leverages Khepri C2 for post-infection operations. Capabilities include file transfer, process execution, system reconnaissance, and command execution, making it a powerful backdoor tool.
By employing the Khepri framework, which is commonly associated with threat actors, the malware integrates sophisticated features like heartbeats to the C2 server at intervals and dynamic C2 configurations to avoid detection.
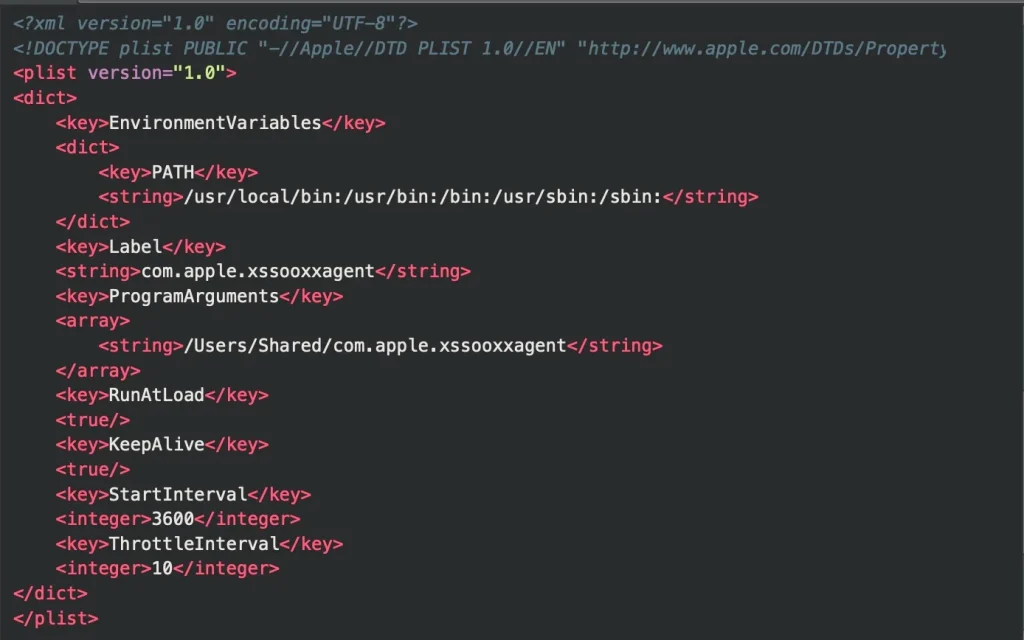
The malware establishes persistence by creating a LaunchDaemon (com.apple.xssooxxagent) in /Library/LaunchDaemons/. It ensures frequent execution by scheduling itself via macOS's built-in task management.
Notably, the .localized binary uses an older API, AuthorizationExecuteWithPrivileges, to request elevated privileges—a deprecated method that bypasses modern security checks.
For detection evasion, the malware employs obfuscation techniques, including a custom XOR-based decryption routine for downloading and verifying new payloads. This allows the creators to update malicious components dynamically while concealing their activities from standard monitoring tools.
Ms. Nivedita Murthy, Senior Staff Consultant at Black Duck, urged caution towards the evolving ZuRu Trojan, which is being embedded in legitimate software. “When updating software, a thorough review should be conducted to ensure that it doesn't introduce new, undocumented functionality or compromise company data,” Murthy added.
Renfrow underlined that EDR tools capable of behavioral analytics like CrowdStrike Falcon, SentinelOne, or eSentire can also provide “visibility into privilege escalation, persistence, and lateral movement.”
To counter threats like macOS.ZuRu malware, users must implement comprehensive cybersecurity measures. Practices include downloading apps only from verified sources, maintaining up-to-date macOS versions, and employing endpoint protection platforms adept at detecting TTPs (Tactics, Techniques, and Procedures) associated with such malware.