Largest Password Breach Compilation Surfaced, Mixing 16 Billion Credentials from Various Companies
- The largest password breach yet is made of 16 billion exposed login credentials from various services.
- Several leaked databases were discovered, which possibly included a huge amount of Apple, Facebook, and Google passwords.
- Yet, these login details seem to be attributed to older breaches and infostealer infections instead of new intrusions.
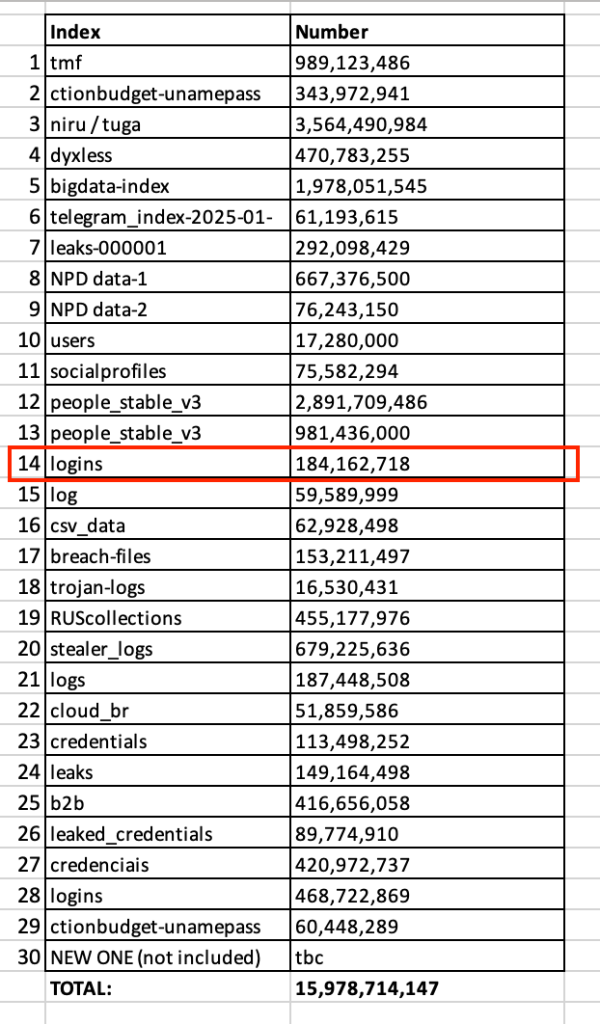
A record-breaking data breach was discovered in the form of 30 exposed databases that made up a large set of possibly already-leaked credentials, primarily stolen through infostealer malware, previous data breaches, and credential-stuffing attacks.
The datasets were temporarily accessible through unsecured Elasticsearch or object storage instances and discovered by Cybernews.
Industry stakeholders argue that there is no evidence this collection includes new or previously unseen data and has likely been circulating for years, with cybersecurity researchers or threat actors having likely aggregated these briefly exposed credentials into a single source.
Security expert Bob Diachenko offered insight on the matter and confirmed there was no centralized breach at Facebook, Google, or Apple, but credentials in infostealer logs contained these companies’ login URLs.
Cybernews revealed proof that some datasets include URLs of Facebook, Yahoo, Google, GitHub, Zoom, Twitch, and other login pages.
Infostealers are lightweight malware programs designed to extract credentials, cryptocurrency wallets, and other sensitive data from infected devices. Once gathered, the stolen data is stored in "logs," archived files that often end up being sold on underground forums or distributed freely online.
While this leak may not be a new breach, it highlights the growing scale of cybersecurity threats surrounding compromised credentials. The latest huge infostealer breach was the 2024 Snowflake customer data leak.