Librarian Ghouls APT Targets Russian and CIS Data and Deploys Crypto Miners
- The latest Librarian Ghouls campaign delivers malicious email attachments and deploys malware.
- The campaign leveraged legitimate tools like AnyDesk and Windows utilities to ultimately mine cryptocurrency via XMRig.
- Attacks added the deployment of remote access tools and the use of phishing sites for email account compromise to data exfiltration.
The Librarian Ghouls advanced persistent threat (APT) group, also known as “Rare Werewolf” or “Rezet,” has been targeting entities across Russia and the Commonwealth of Independent States (CIS) with a sophisticated campaign involving data theft and cryptocurrency mining.
Active as of May 2025, their tactics highlight a noteworthy reliance on legitimate third-party software to execute malicious objectives covertly, a recent analysis by Kaspersky reveals, shedding light on their persistent operations.
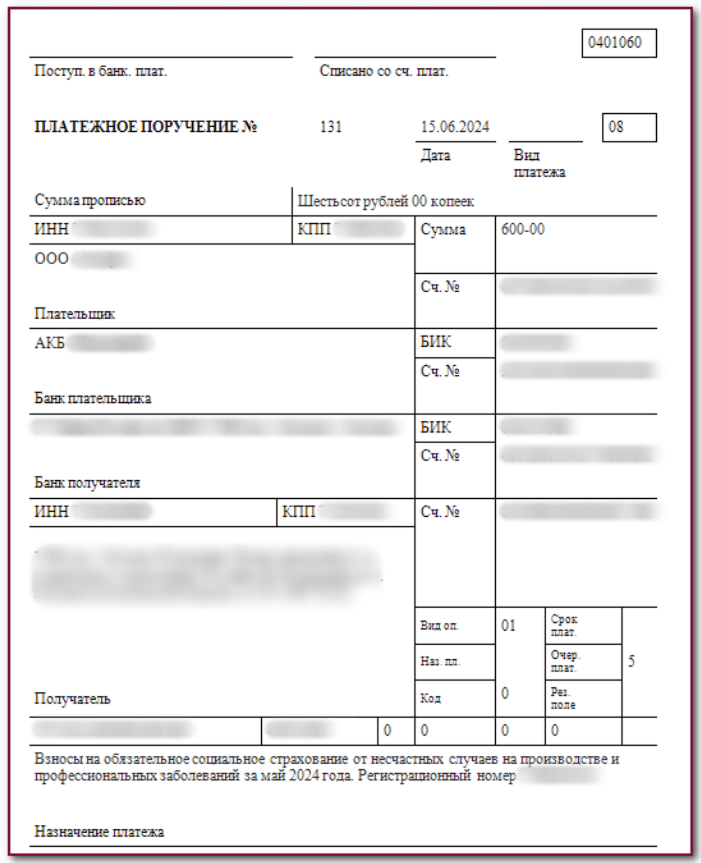
The attack starts with targeted phishing campaigns, where victims receive password-protected archives disguised as legitimate business documents, such as PDF invoices or payment orders. These archives contain malicious payloads that infiltrate systems when executed.
Once infected, the attackers deploy legitimate utilities like AnyDesk and Windows utilities, alongside bespoke PowerShell scripts and BAT files.
These tools allow Librarian Ghouls to disable system defenses, establish remote access to victim devices, and exfiltrate sensitive data like credentials and cryptocurrency wallet information.
A particularly unique aspect of the campaign is the installation of XMRig, a widely known crypto mining tool, with attackers using detailed system data, such as GPU and RAM specifications, to optimize mining operations.
Unlike other APT groups relying on custom malware binaries, Librarian Ghouls utilize well-known tools, including Mipko Personal Monitor, Blat SMTP, and ngrok, among others. Their strategic use of legitimate software complicates detection and attribution efforts.
While primarily targeting Russian industrial enterprises and engineering schools, this campaign has also reached victims in Belarus and Kazakhstan. Most phishing assets, including decoy documents and malicious archives, are tailored specifically for Russian-speaking users.