DarkGaboon Targets Russian Companies with Advanced Tactics, Deploys LockBit Ransomware
- The DarkGaboon APT recently displayed sophisticated attack vectors and toolsets.
- New reports indicate the threat actor intensified its phishing campaigns targeting Russian entities.
- Revenge and XWorm RAT trojans and LockBit 3.0 are deployed via fake email attachments.
The financially motivated APT group DarkGaboon has intensified its assaults on Russian companies, refining its tactics, techniques, and procedures (TTPs) since its discovery earlier this year.
Investigations by Positive Technologies’ Threat Intelligence division have unveiled the group’s continued focus on email phishing campaigns, deploying increasingly sophisticated malicious payloads.
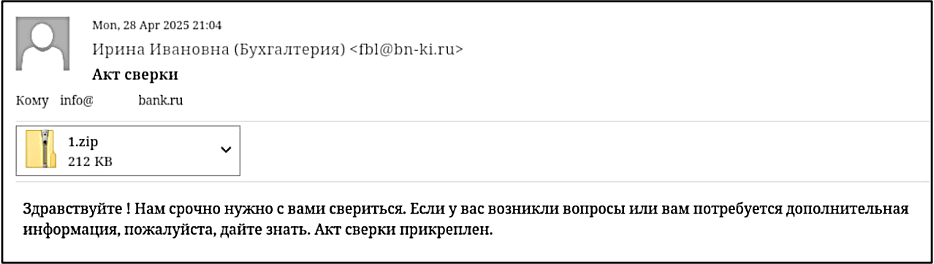
DarkGaboon’s campaigns rely on cleverly designed phishing emails targeting financial departments within organizations. These emails use Russian-language urgency-based narratives and contain malicious attachments disguised as legitimate financial documents.
The emails include archives containing RTF decoy documents and .scr files. These files are heavily obfuscated using advanced techniques such as Themida and .NET Reactor, and deploy well-known Remote Access Trojans (RATs) such as Revenge and XWorm.
To enhance deception, homoglyph file names, fake PDF document images, and invalid X.509 certificates purportedly issued in the name of Russian companies or referencing accounting contexts are used.
One notable development is the group’s method of acquiring templates. The malicious RTF decoy documents have been downloaded from legitimate resources offering financial document templates. This approach has provided consistency and cover for DarkGaboon since early 2023.
Once inside the network, the group employs tools like the N.S. network scanner to identify and access shared resources.
Additionally, ransomware LockBit 3.0 is used to encrypt critical files, with a ransom note detailing decryption instructions left behind. Surprisingly, there is no visible evidence of data exfiltration before encryption, a deviation from typical ransomware behavior.
DarkGaboon maintains a dynamic network infrastructure. It leverages compromised domains and Dynamic DNS services for command and control (C2) operations, hosting many of its systems with international hosting providers.
ATT&CK pattern analyses reveal the group’s ability to evade detection and erase digital footprints, underscoring its operational sophistication.