BladedFeline Campaign Unveiled Targeting Kurdish and Iraqi Government Officials
- An Iran-aligned cyberespionage group is reportedly behind a campaign targeting officials in Kurdistan and Iraq.
- The threat actor uses reverse tunnels, auxiliary tools, a backdoor, and a malicious IIS module.
- By using highly tailored malware and maintaining operational secrecy, the group poses a threat to Middle Eastern governments.
BladedFeline, a sophisticated Iran-aligned cyberespionage group, has systematically targeted Kurdish and Iraqi government officials for years, leveraging advanced malware and persistent tactics to maintain access and facilitate data exfiltration.
The campaign, active since at least 2017, demonstrates the rapidly evolving threat landscape in the Middle East, especially among government and diplomatic sectors, ESET Research has uncovered.
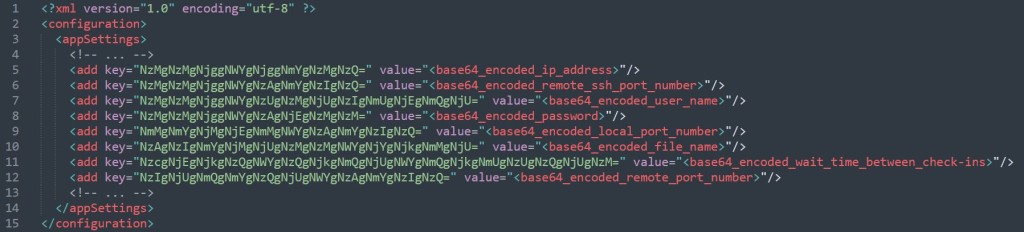
BladedFeline’s toolkit has expanded well beyond early implants, such as Shahmaran, to include advanced malware such as the Whisper backdoor and the PrimeCache malicious IIS module.
The group has consistently focused on high-value targets, including the Kurdistan Regional Government (KRG) and Iraq's central government, and more recently extended its reach to a regional telecommunications provider in Uzbekistan.
ESET’s analysis has identified significant code and operational overlaps between BladedFeline and OilRig, a known Iran-aligned advanced persistent threat (APT) group, leading researchers to conclude with medium confidence that BladedFeline functions as a subgroup within OilRig.
Notably, the PrimeCache malware shares architectural features with OilRig’s RDAT backdoor, while the group’s operational infrastructure and target profiles mirror OilRig’s well-documented tactics.
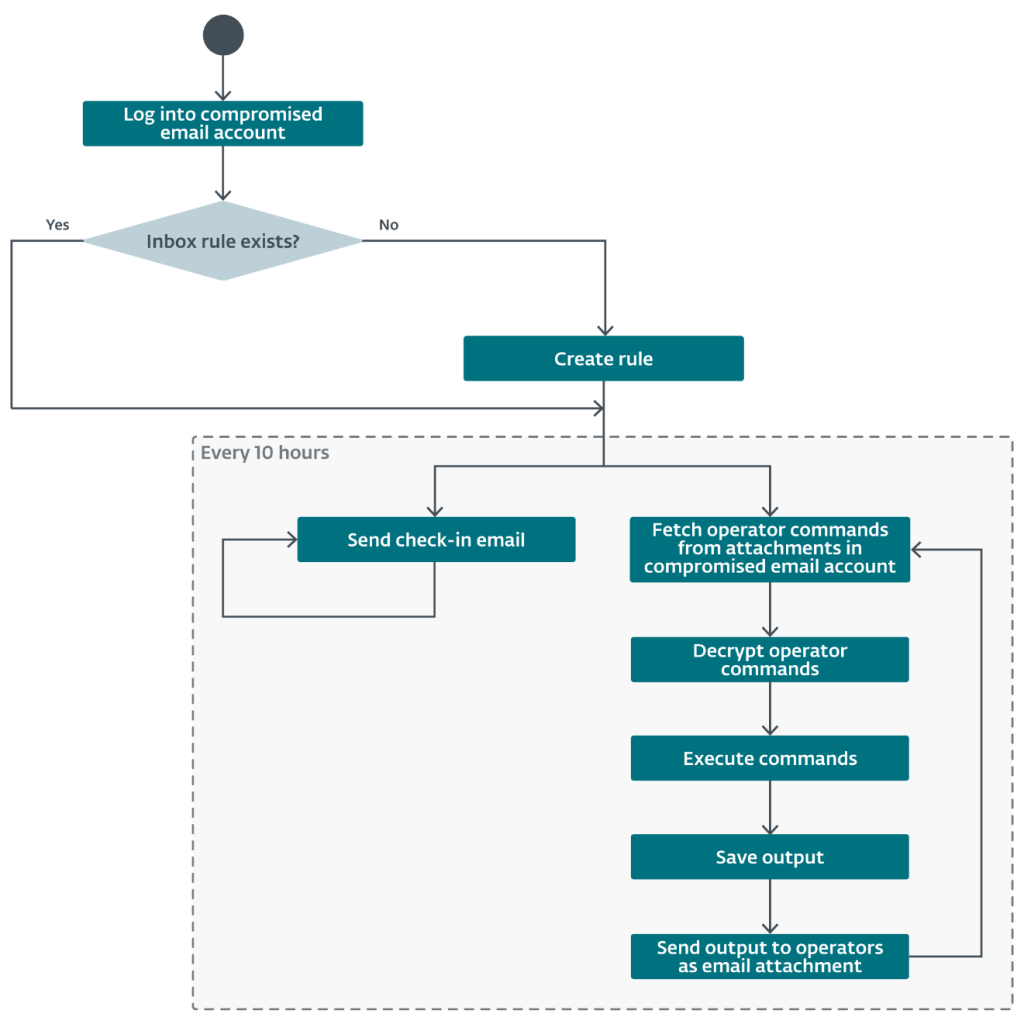
The Whisper backdoor communicates via email attachments on compromised Microsoft Exchange accounts, enabling attackers to execute commands, transfer files, and evade traditional network monitoring.
PrimeCache IIS module acts as a covert backdoor, processing commands received as cookies in HTTP headers, and facilitating persistent access, data exfiltration, and file manipulation on compromised servers.
The use of tools like Laret, Pinar, Flog webshell, and Hawking Listener underscores the group’s emphasis on maintaining long-term access and minimizing detection.
The campaign leverages execution on system startup, custom PowerShell scripts, and timestomping techniques to evade forensic analysis and ensure ongoing access.
BladedFeline’s sustained operations against the KRG and Iraq highlight the strategic value Iranian APTs place on regional influence, sensitive diplomatic relations, and critical infrastructure.