UNC6040 Targeting Salesforce via Sophisticated Vishing Campaigns
- GTIG tracked a complex voice phishing campaign targeting Salesforce via Mullvad VPN IPs.
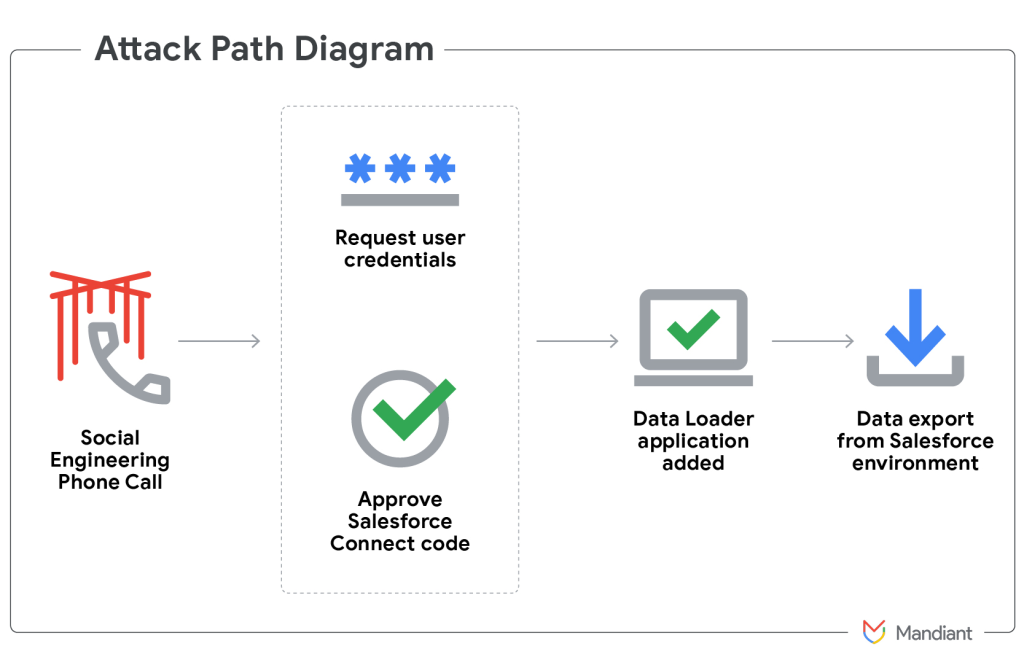
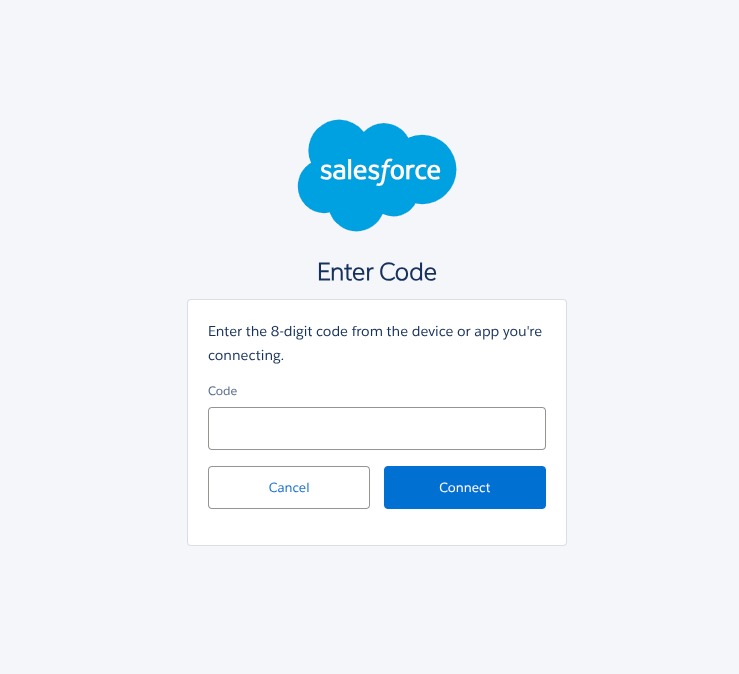
- UNC6040 persuades users to approve a malicious connected app during vishing sessions.
- Attackers often deliver a modified version of Salesforce’s Data Loader, masked under alternate names such as “My Ticket Portal.”
The Google Threat Intelligence Group (GTIG) has detailed an ongoing investigation into UNC6040, a financially motivated threat actor cluster that has engineered notable voice phishing (vishing) campaigns targeting organizations’ Salesforce environments.
Over recent months, UNC6040 has demonstrated considerable success in compromising corporate networks, utilizing refined telephone-based social engineering methods to impersonate IT support and deceive employees, particularly within English-speaking branches of multinational organizations.
Rather than exploiting software vulnerabilities, UNC6040’s operators meticulously manipulate end users. A prevalent tactic involves persuading victims to approve a malicious connected app within their Salesforce portal during vishing sessions.
Attackers often deliver a modified version of Salesforce’s Data Loader, masked under alternate names such as “My Ticket Portal,” and guide targets to authorize its connection. This grants the threat actor extensive access privileges, enabling rapid and large-scale exfiltration of sensitive Salesforce data.
The abuse of the Data Loader is consistent with recent security advisories from Salesforce.
Following the Salesforce compromise, UNC6040 has exhibited the capability to move laterally, using harvested credentials and multifactor authentication codes to target additional cloud environments like Okta and Microsoft 365.
The group’s infrastructure is notable for its use of Mullvad VPN IP addresses and customized phishing panels, including interfaces designed to obtain further authentication inputs from victims.
Some extortion demands linked to these breaches have surfaced months after initial access, indicating that UNC6040 may collaborate with secondary actors tasked with monetizing stolen data.
During extortion, UNC6040 affiliates have claimed ties to the ShinyHunters group, likely in an attempt to amplify the psychological pressure on victims.
Infrastructure and tactics display similarities to threat collectives linked with “The Com,” suggesting shared methodologies within overlapping cybercriminal communities, rather than direct collaboration.
Google says that UNC6040’s activities reinforce the trend of targeting IT support personnel through social engineering as a primary ingress vector for enterprise data compromises. With an extended dwell time before extortion, organizations may not realize the extent of compromise for months, increasing operational risk.