Misconfigurations Across Seven Cloud Providers Expose 660K buckets, 200B Files, 110K Credentials and More
- Researchers pulled credentials, internal backups, and source code from exposed cloud buckets
- Over 200 billion files across seven cloud providers have been found publicly exposed
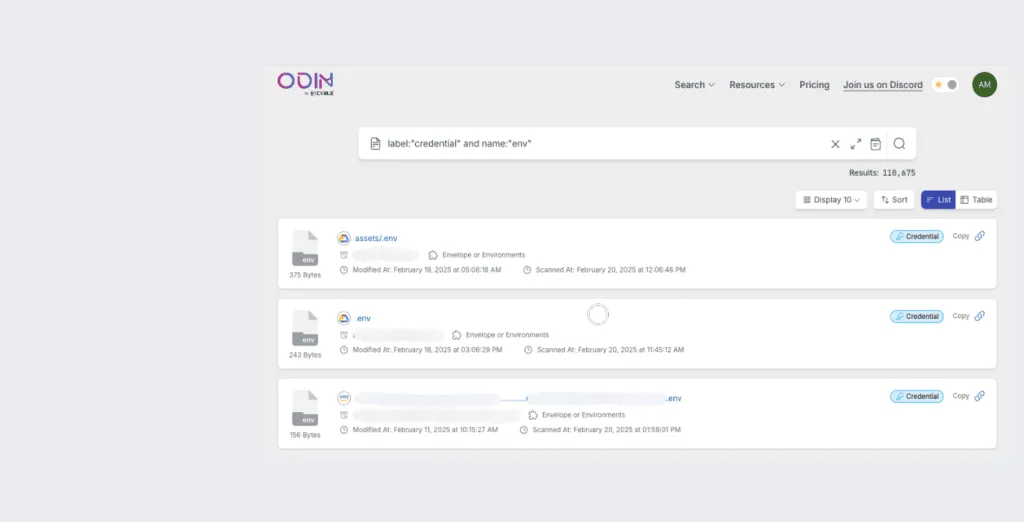
- 91M hosts, 660K buckets, and 110K env credentials left unprotected due to misconfiguration
Researchers discovered over 200 billion exposed files spanning seven cloud providers left accessible to the public due to misconfigurations. Exposed cloud buckets are a treasure trove for threat actors, especially if the information includes login details, backups, and source codes.
Odin, an internet scanning platform by Cyble, also found over 660,000 exposed buckets and over 91 million exposed hosts in its scan, which uses a machine learning-based detection model.
The exposed files contained several types of sensitive data. A search for credentials led to 110,000 results.
About 1.6 million files with confidential information were retrieved from the publicly accessible database. And 5.6 million files for the Go language were extracted from the 200 billion exposed files in cloud buckets.
The data type points to the threat hovering over the owners and users of the data. Cybercriminals thrive on data extracted from the exposed cloud bucket files.
Publicly accessible cloud storage buckets can be leveraged as an attack vector, gaining access to admin account credentials, increasing privileges, and bypassing security mechanisms put in place.
Breaching or exploiting cloud infrastructure has allowed cybercriminals to gain asset visibility and contributed to over 23% of the data breaches in late 2024.
Cloud services fuel businesses globally; however, it calls for a robust security protocol and safeguards against human errors.
“While cloud storage is typically private by default, it can quickly get complicated when you start sharing objects or resources,” Cyble noted. Conducting security audits and maintaining access control to cloud buckets is necessary to avoid leaving sensitive information exposed publicly.
To address the complexity involved in the auditing process arising from using both Identity and Access Management (IAM) and Access Control Lists (ACLs), businesses opt for assigning access controls on a ‘per-object’ basis.
However, this approach is not foolproof, leaving them with another option of using managed folders. It further limits access to specific groups of objects in a bucket.