Hamilton County Sheriff’s Office Allegedly Breached By Qilin Ransomware Group
- The Qilin ransomware group claimed to have targeted the Hamilton County Sheriff’s Office
- They allegedly exfiltrated 99 GB of data containing 128,294 files
- The group did not post any samples of stolen data from the data breach
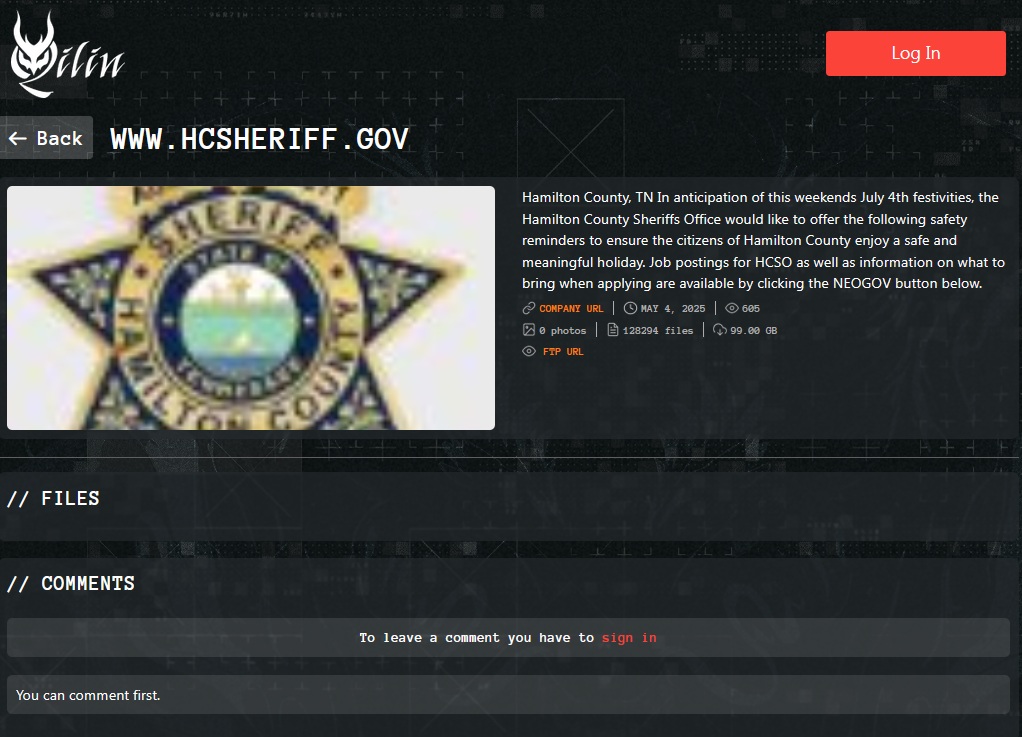
The Hamilton County Sheriff’s Office of the USA has been named a victim of a ransomware attack on the dark web. The Qilin ransomware group posted on its dark web portal about the incident.
According to threat intelligence, the group exfiltrated nearly 99GB of data allegedly from the www.hcsheriff.gov website. The exfiltrated data amounted to 128,294 files.
The ransomware attack announcement was published on May 4, 2025, and received over 600 views from the platform users. They had not posted any samples or photos as proof of the alleged security incident.
The veracity of the claims has not been established yet, nor has the Hamilton County Sheriff’s Office commented on it. We approached the officials for a statement and will update this report after receiving a response.
The Hamilton County Sheriff’s Office is coping with the tragic loss of its deputy, who was intentionally run down by a man with his car yesterday.
In another incident, the INC ransomware group claimed to have targeted the Cleburne County Sheriff’s Office.
Qilin has become a growing threat to digital infrastructure and recently reached the top position in the ransomware ladder. Qilin is followed by Akira and Play ransomware groups taking the second and the third position.
Despite the ranking of adversaries, law enforcement agencies have made major strides in dismantling the infrastructure of threat actors, with the latest one being the DDoS services crackdown and arrest of prime suspects running DDoS-for-hire platforms.
Qilin, also known as Agenda, has been active since 2022 and operates as a ransomware-as-a-service entity, allowing other threat actors to subscribe to use its tools. The group boasts capabilities like tailoring its encryption methods to the needs of the buyers, restarting systems in Safe Mode. and offering various execution parameters.
They use valid account credentials to gain access through leaked credentials from previous hacking attempts.