LockBit Ransomware Gang Affiliates Breached, Victim Negotiations Exposed
- LockBit affiliates’ dark web panels and databases were reportedly defaced and breached, respectively.
- The message displayed on the infiltrated platforms is similar to one used in a recent Everest ransomware leak site defacement.
- Leaked data includes Bitcoin addresses, build configurations, negotiation chats, and user database.
The LockBit ransomware gang, notorious for its prolific cyberattacks, suffered a breach of its affiliate forums and databases, which exposed critical operational details. The attack targeted LockBit’s dark web affiliate panels.
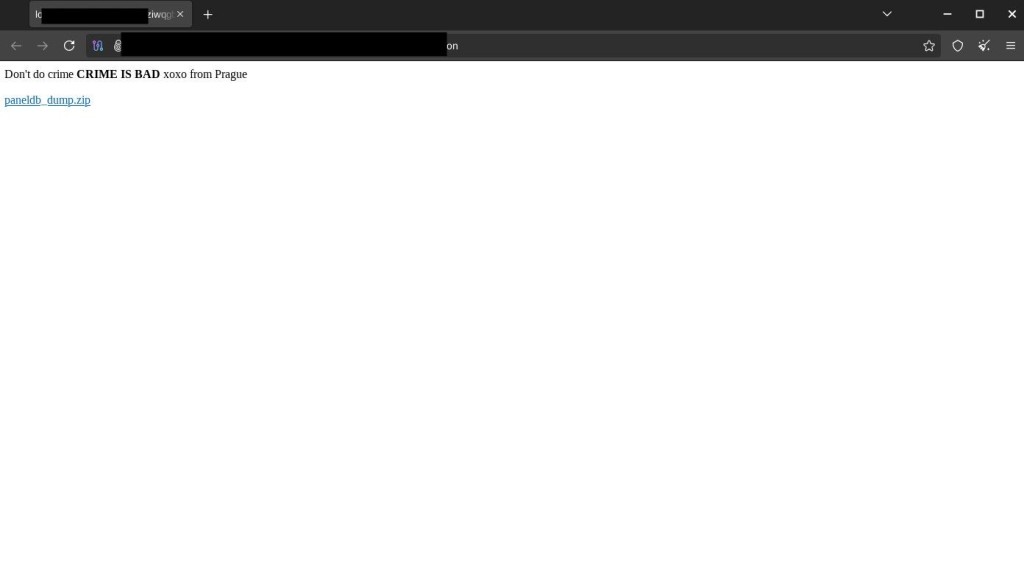
Attackers defaced the site with a message reading, “Don’t do crime CRIME IS BAD xoxo from Prague,” alongside a link to a MySQL database dump file. The same message was seen on the defaced leak site of the Everest Ransomware gang in April 2025.
The leaked data reveals various internal operations, including:
- Bitcoin Addresses (59,975 unique entries): An insider glimpse into the financial structure of LockBit's ransomware activities.
- Affiliate Build Configurations: Details such as encryption targets and operational preferences for affiliates.
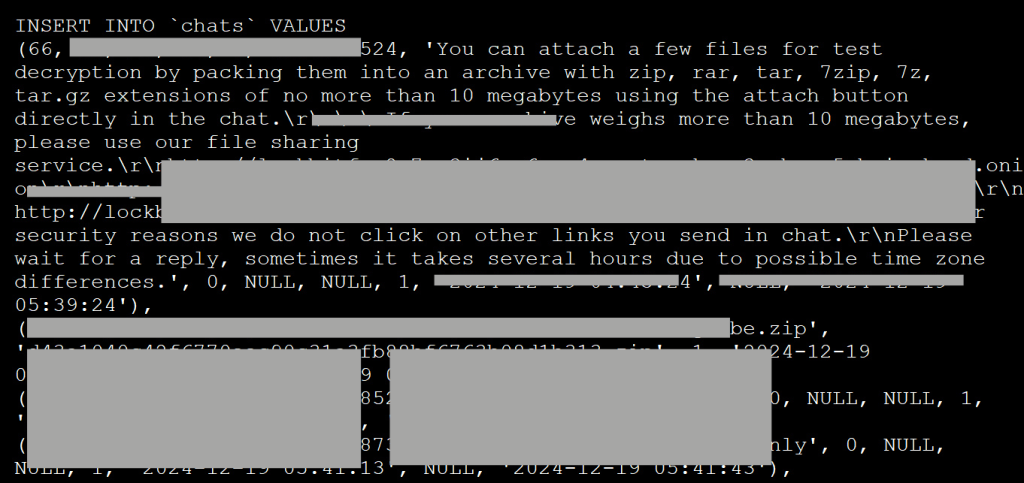
- Negotiation Chats (4,442 entries): Insights into dialogues between the gang and ransomware victims from December 19 to April 29.
- User Database (75 listings): Includes plaintext passwords of affiliate users, including usernames like "Lockbitproud231" and "Weekendlover69."
Known for its global footprint of operations, Everest ransomware is a Russia-linked threat actor responsible for numerous data breaches targeting enterprises and government organizations.
The LockBit server was running PHP version 8.1.2, which is exposed to the critical vulnerability CVE-2024-4577. This exploit allows remote code execution, making it a likely vector used by the attackers.
The LockBit operator, known as "LockBitSupp," confirmed that affiliate panels were indeed hacked but claimed that no private keys or critical operational data were leaked. Despite these assurances, the timing of the database dump and its public exposure undermine the gang’s reputation and operational secrecy.
This development added another layer to the challenges already faced by the group following law enforcement actions in recent years.