Mass Scanning by Proton66, Connection with Prospero, Chang Way Technologies, Bulletproof Services, and Blocked IPs
- Researchers found evidence to prove a connection between Proton66 and Chang Way Technologies
- Net blocks were observed for brute force attacks including IP addresses with no crime history
- Threat actors leveraged WordPress to target organizations across the globe
Researchers observed an increase in the malicious traffic coming from a specific IP address associated with the SuperBlack ransomware. The traffic originates from Proton66 ASN exploiting organizations around the world via multiple malware campaigns leveraging WordPress websites.
The campaign involves redirecting Android devices to fraudulent Google Play stores and exploiting Korean-speaking chat room users. Researchers noticed a spike in mass scanning attempts and brute forcing starting January 8, 2025.
Statistical data for the months of January, February, and March revealed that technology and financial organizations were the most targeted. They also targeted non-profits and engineering firms.
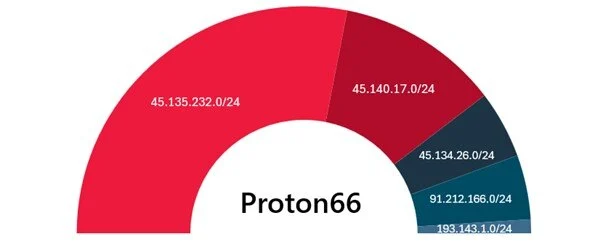
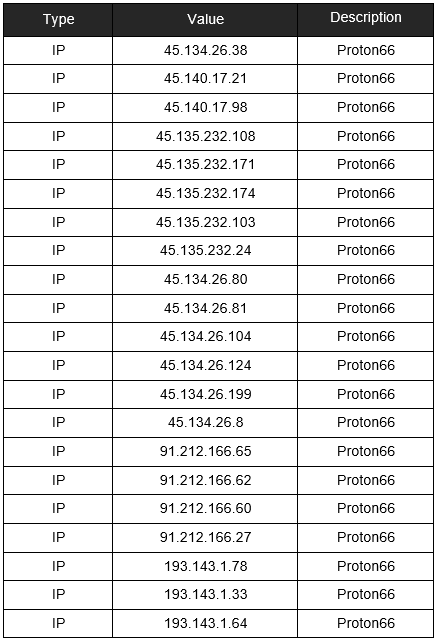
Five net blocks were listed on blocklists of Spamhaus and others for malicious activity traced AS198953 which belongs to Proton66 OOO. The triple is the Russian version of LLC.
The net blocks 45.135.232.0/24 and 45.140.17.0/24 launched brute force attacks and mass scanning. Among the traced IP addresses were those that had no previous history of malicious activity and those that remained inactive for two years or more.
AbuseIPDB marked the IP addresses 45.134.26.8 and 45.135.232.24 for suspicious activity in November and July 2021.
The Trustwave report noted that its customers were also targeted with failed attempts in this campaign.
The report read, “All of our customers were protected as the scanning and exploit attempts were blocked.”
In February, their activities reduced in number however, The SuperBlack ransomware IP 193.143.165 revealed the exploitation of the recent critical vulnerabilities including:
- The authentication bypass in the web interface of Palo Alto Networks’ PAS-OS software: CVE-2025-0108. The following URL was observed in exploit attempts:
GET /unauth/%252e%252e/php/ztp_gate.php/PAN_help/x.css
- CVE-2024-41713 in Mitel MiCollab 9.8 SPI FP2 (9.8.1.201) which would allow threat actors to launch a path traversal attack. The URL attempting to exploit the same was:
GET /npm-pwg/..;/axis2-AWC/services/listServices
- The command injection vulnerability CVE-2024-10914 affects D-Link NAS models that have reached their end of life. The URL found in this flaw exploitation was:
GET /cgi-bin/account_mgr.cgi?cmd+cgi_user_add&name=’;<removed>;’
The IP address of SuperBlack was associated with another ransomware operator who is suspected to be an initial access broker named Mora_001. They were found exploiting bugs in Fortinet FortiOS-based devices.
Moreover, the SuperBlack ransomware shares similarities with the LockBit 3.0 operating as a Ransomware-as-a-Service (RaaS) model with slight differences in their ransom notes and data exfiltration executable.
Proton66 has been involved in mass scanning and using the WeaXor ransomware. Instances of the group using bulletproof services for anonymity similar to the Russia-based service provider PROSPERO (AS200593) that sells malicious software, and botnet controllers.
The bulletproof services are offered on forums named Securehost, UNDERGROUND, and BEARHOST among others. Threat actors negotiate malware purchases on their Telegram and Jabber accounts that operate in Russian and English language.
In December 2024, the malicious services offered by BEARHOST and UNDERGROUND disappeared which led to the forum members to inquire about the same. Following which a user named VOODOO SERVERS informed them that they will offer their services through a private company.
Researchers found that BEARHOST interacted with Hong Kong-based Chang Way Technologies Co. Limited.
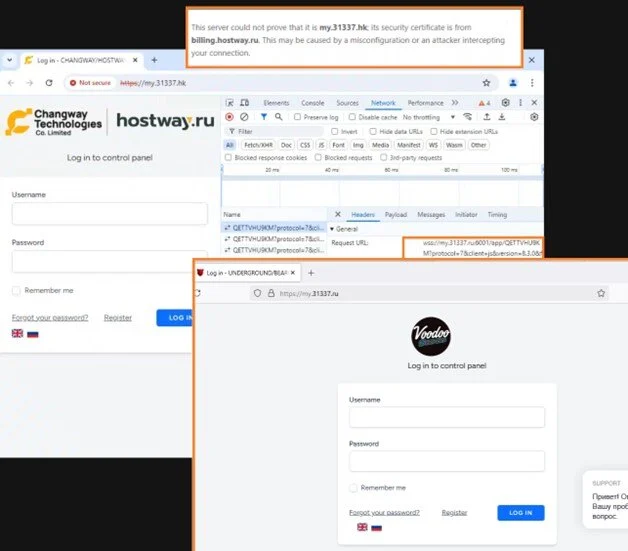
“While the Russian hosting control panel used by UNDERGROUND BEARHOST customers, my.31337.ru, remained unchanged, my.31337.hk page was updated to a new CHANGWAY / HOSTWAY theme,” SpiderLabs researchers revealed.
They also found a websocket connection to my.31337.ru:6001 opened by the panel application script that appeared in the background. Evidence also revealed a certificate from billing.hostway.ru furnished by my.31337.hk.