“Goontact” Is a Novel Spyware Disguised as a Secure IM App
- Sextortion actors are luring victims on fake websites that spread spyware in the form of cloned IM apps.
- The target audience involves mostly people from Southeast Asian countries.
- The actors somehow manage to take care of iOS certificate signing, abusing Apple’s business program.
“Goontact” is a new spyware that’s spreading like wildfire in the Android and iOS platforms, disguised as Telegram, Signal, KakaoTalk, and various apps used for accessing escort services. The malware can exfiltrate highly sensitive details from its victims’ devices such as their contacts lists, SMS messages, photos stored on external storage (SD card), their location, device identifiers, and the phone number. This is typically used for a targeted extortion campaign that follows afterward, possibly carried out by different actors who are buying the information from the Goontact operators.
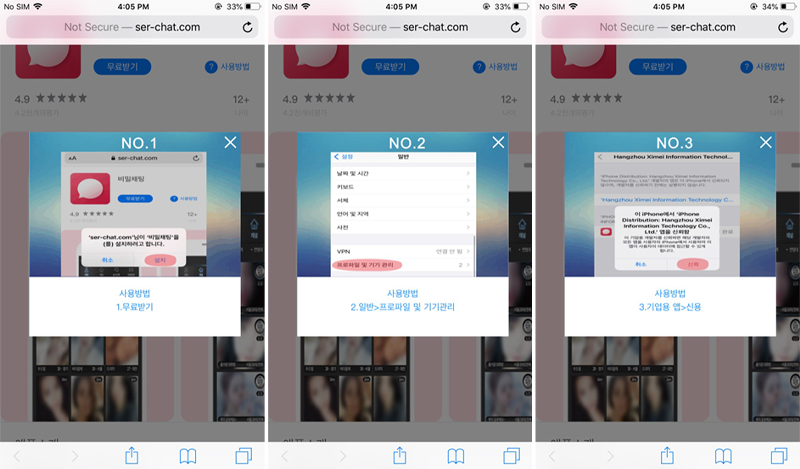
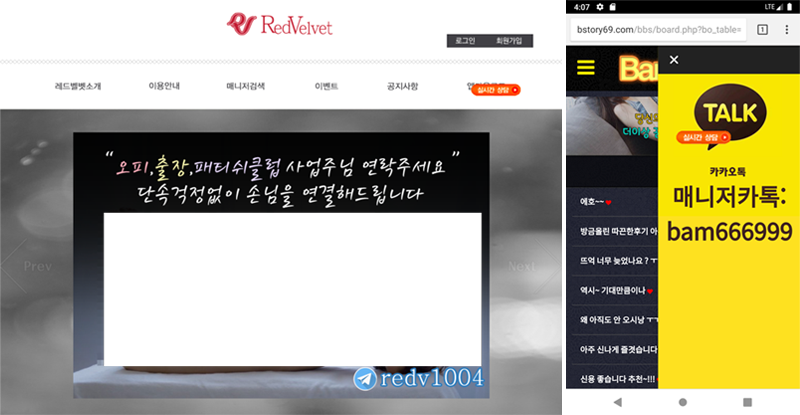
Lookout researchers have analyzed the relevant campaigns and report having recorded sextortion scams targeting Chinese, Japanese, Korean, Thai, and Vietnamese users. The victims are lured on one of the websites given in the below image and are urged to install a supposedly “secure communication” app. In reality, the apps are just malware, and the victims are not communicating with women but with the scammers themselves.
Interestingly, the actors are abusing the IPA distribution system and using valid enterprise certificates to sign their malicious packages, so the malware infections take place unobstructively while giving a sense of legitimacy.
Normally, Apple would never give these crooks a valid certificate, so they’re either stealing it from a business or somehow tricking the reviewers. The Lookout team has found that the company names used are real and match App Store developers, but it’s still unclear whether these developers have been compromised or if they operate as masqueraded agents.
On the Android space, an APK file needs to be downloaded and installed manually, and the actors are providing detailed instructions on how to do that and how to “enable untrusted sources.” Having done that, there’s nothing else to stay in the way of the spyware. Notably, on Android, SMS and location data are exfiltrated to the C2, whereas on the iOS version of Goontact, these two elements have not been implemented.
If there’s one key takeaway from this, that would be to only trust apps found on the official app stores. Even then, you cannot be too sure, and you should never be.
An indication about the “spyware” nature of the above apps would be the number and type of permissions requested upon installation, but this can be easily overlooked when someone focuses on the promise rather than the means. There are legitimate escort service apps on the App Store and the Play Store, so you really have no reason to trust obscure sources.