“PhantomLance” Has Infiltrated the Google Play Store More Than Once
- PhantomLance has infected Google Play Store users in at least three separate incidents.
- The latest campaign entered the official Android market last November and used a system cleaner application.
- The actors behind seem to be the OceanLotus/APT32, and the motives are very specific.
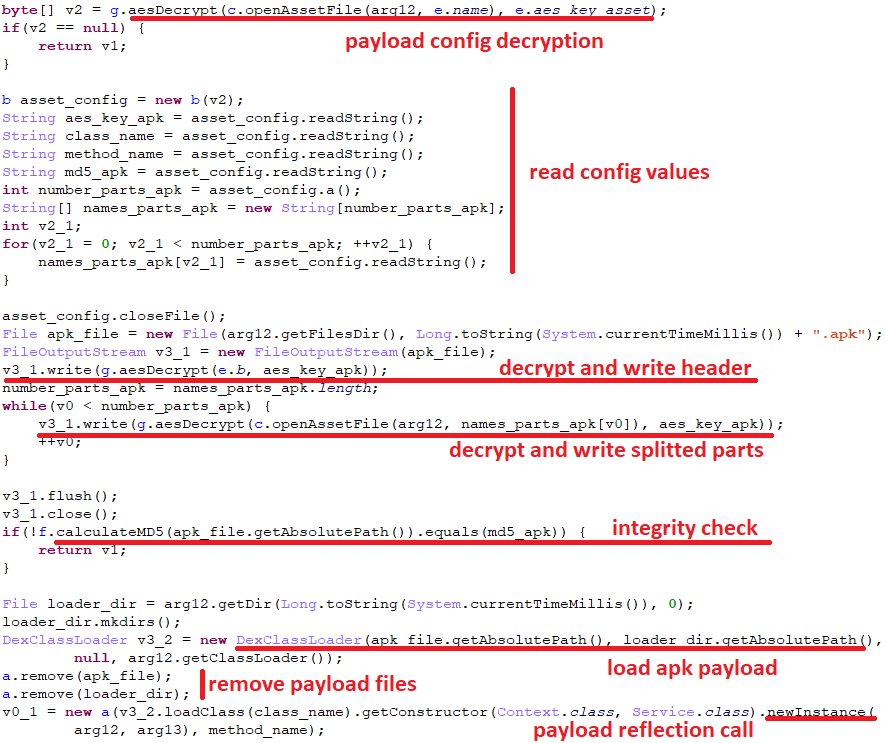
The “PhantomLance” malware that has been around since at least 2015 is now confirmed to have infiltrated the Google Play Store multiple times, the last time being on November 6, 2019. Although Google has removed it from Android’s official app marketplace, it is very likely that millions of devices remain infected. PhantomLance has used numerous “trojan horse” apps to find its way into the Play Store over the years, with the most recent example being a supposed browsing history and file system cleaned named “Browsers Turbo.”
Source: SecureList
Kaspersky researchers, who have conducted an in-depth investigation on the appearance of “PhantomLance” on the Play Store, talk about three versions of different levels of complexity and feature sophistication. These versions didn’t appear in a natural order but instead were planted on apps in a somewhat unorthodox manner. For example, version 3 circulated between 2016 and 2018, while version 2 was deployed afterward. All specimens though feature some common capabilities, which can be summed up in the following:
- Get device information (model and OS)
- Get a list of the installed applications
- Access and exfiltrate SMS communications
- Access and exfiltrate geo-location data
- Access and exfiltrate call logs
- Fetch additional payloads from the C2
According to the Kaspersky report, the C2 server infrastructure that is used to support PhantomLance operations is not linked to any other known malware samples, so it’s a dedicated network. After checking where the parent domains resolve, the researchers found the 188.166.203[.]57 IP address, which belongs to the cloud infrastructure services provider DigitalOcean. Upon further investigation, the team figured that some websites hosted by the same provider overlap with the “OceanLotus” APT32 infrastructure. In addition to this, there are code structure similarities between PhantomLance v3 and older OceanLotus campaigns on Android, so there’s a concrete connection here with the Vietnamese hacking group.
Source: SecureList
Some of the most targeted countries are India, Vietnam, Bangladesh, Indonesia, Nepal, Myanmar, and Malaysia. Other apps that were laced with PhantomLance in the past are “Dia Diem Nha Tho,” “Ads Skipper v2,” and “Cham soc be yeu | BabyCare.” These emphasize the targeted nature of the campaigns, as we’re talking about apps that are used by particular categories of people, and thus target a narrow audience. The “Dia Diem Nha Tho,” for example, provides information about Christian churches and priests in Vietnam. Only about 7% of the population of Vietnam are Catholics, so we have a very specific targeting example right there.