46 Qualcomm Chips Found To Be Vulnerable to Encryption Keys Retrieval
- Researcher finds a severe flaw in Qualcomm’s QSEE which provides a pathway for key-grabbing side-channel attacks.
- The vulnerability affects 46 Qualcomm chips, used in an extensive range of smartphones and tablets.
- Android April security update pushed the relevant patch, but the majority of users are unlikely to have received it yet.
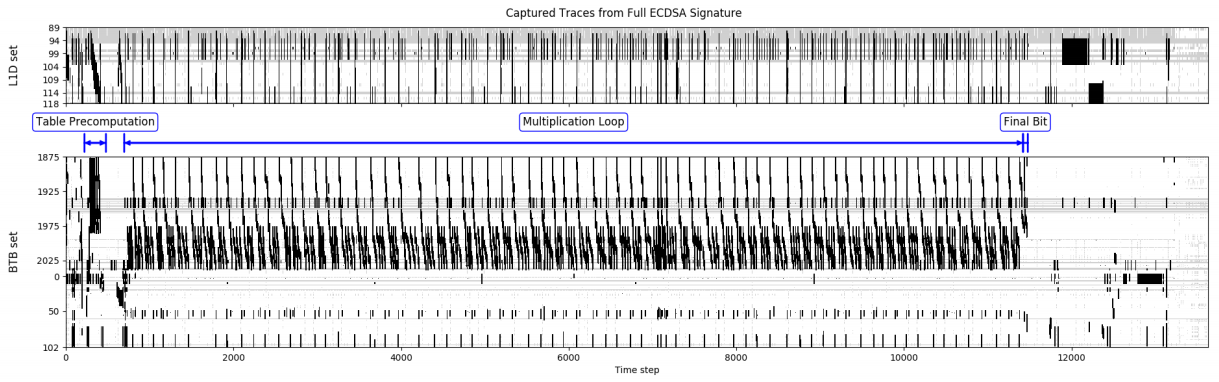
A broad spectrum of Qualcomm chips that are used in millions of devices around the world is found to be vulnerable to a severe flaw (CVE-2018-11976) in the Qualcomm Secure Execution Environment (QSEE). Discovered and disclosed by Keegan Ryan, Senior Security Consultant of the NCCGroup, this vulnerability allows someone to retrieve data that is processed inside the QSEE, as long as the attacker has root access on the device. The researcher used a memory cache analyzer and found two leaking points on the QSEE which were giving out enough data to recover 256-bit ECDSA keys.
Image source: qualcomm.com
The QSEE is supposed to be a location where very security-critical activities take place. It is Qualcomm’s implementation of a “Trusted Execution Environment” (TEE) which is usually where applications send their encryption keys and passwords for processing, keeping them safe from possible theft. However, memory corruption flaws are the Achilles Heel of any TEE, and this is precisely where the problem for QSEE lies. The researcher used a Nexus 5X device to recover a P-256 private key from the TrustZone keystore. The recovery was made possible through the capturing of none-bit guesses, and the use of a lattice-based key recovery algorithm.
Image source: NCCGroup Whitepaper
While the QSEE system is ubiquitous, attackers have not given it matching attention yet, and this is also reflected in the study of the feasibility of side-channel attacks against QSEE. The disclosure to Qualcomm occurred back in March 2018, while Qualcomm had a fix ready by October 2018, which is when the relevant patch became available. However, since many smartphone and tablet manufacturers are not pushing out updates for their older devices (and in many cases not even for the newer ones), the QSEE vulnerability is still present on numerous devices out there.
The 49 chips that are affected are the following: IPQ8074, MDM9150, MDM9206, MDM9607, MDM9650, MDM9655, MSM8909W, MSM8996AU, QCA8081, QCS605, Qualcomm 215, SD 210/SD 212/SD 205, SD 410/12, SD 425, SD 427, SD 430, SD 435, SD 439 / SD 429, SD 450, SD 615/16/SD 415, SD 625, SD 632, SD 636, SD 650/52, SD 712 / SD 710 / SD 670, SD 820, SD 820A, SD 835, SD 845 / SD 850, SD 8CX, SDA660, SDM439, SDM630, SDM660, Snapdragon_High_Med_2016, SXR1130.
As you can see, Snapdragon models belonging to series 4, 6, 7, and 8, which currently cover the vast majority of the market, are affected. If you have not received Android’s April security update, then chances are that your device is vulnerable to the CVE-2018-11976.
Have you received the April security update? What device are you using? Share the details below and help us spread the word of warning by sharing this post through our socials, on Facebook and Twitter.