20,000 Malicious Cyber Assets Used in Infostealer Activities Disrupted via INTERPOL’s Operation Secure
- An international operation disabled IPs, C2 servers, and domains used in infostealer activities.
- Several individuals have been arrested in connection with large-scale cyber theft and fraud
- These Interpol-coordinated actions included notifying over 200,000 victims and potential victims.
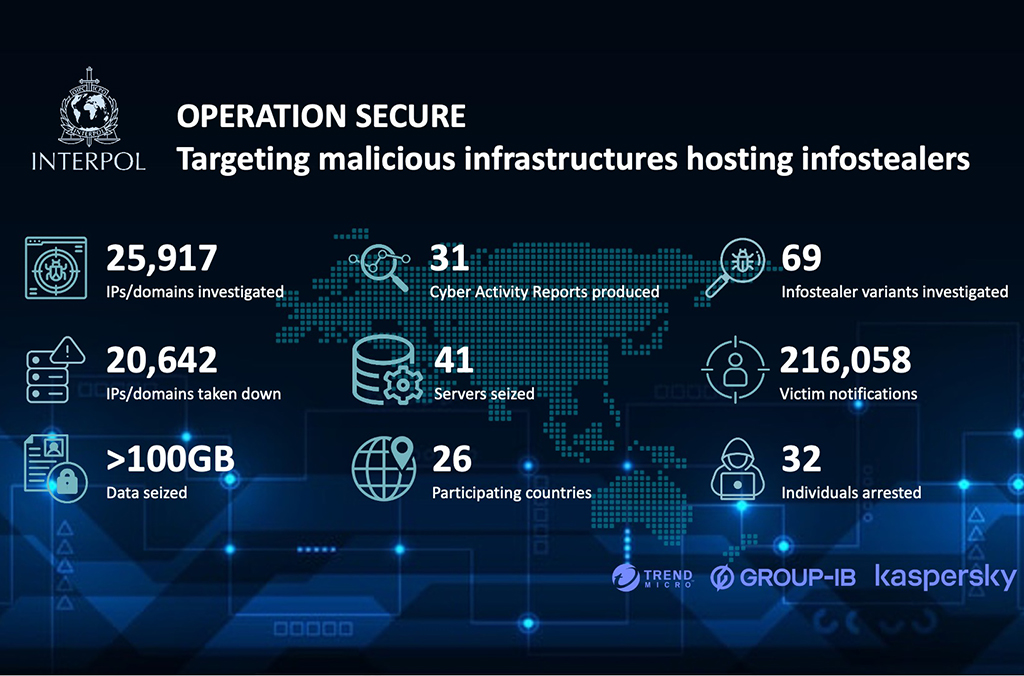
INTERPOL recently launched the cybercrime initiative Operation Secure, which resulted in the seizure of over 20,000 malicious IPs and domains used in infostealer malware activities, as well as over 40 command-and-control (C2) servers.
The infostealer malware at the center of this operation is designed to extract sensitive information like passwords, browser credentials, credit card details, and cryptocurrency wallets.
Authorities noted the seizure of 41 C2 servers and over 100GB of data, arrests of 32 suspects involved in large-scale cyber theft and fraud, and notification of over 216,000 victims and potential victims, encouraging preventive action.
The targeted takedown neutralized almost 79% of identified suspicious assets, significantly reducing cybercriminal networks’ operational capabilities.
Operational highlights include the arrest of 18 cybercriminals by Vietnamese police, uncovering illicit schemes involving cash, SIM cards, and enterprise account sales. Law enforcement in Sri Lanka and Nauru apprehended 14 suspects during house raids, protecting 40 identified victims.
Detailed analysis in Hong Kong led to the discovery of 117 C2 servers spread across 89 internet service providers.
This international crackdown, running from January to April 2025, brought together law enforcement agencies from 26 countries with the shared mission of dismantling the cybercriminal infrastructure targeting sensitive data.
INTERPOL worked closely with cybersecurity partners like Group-IB, Kaspersky, and Trend Micro to produce actionable intelligence that was distributed across Asia.
This initiative, coordinated under the Asia and South Pacific Joint Operations Against Cybercrime (ASPJOC) Project, marks a critical step forward in strengthening regional and global defenses against cybercrime.
After a recent law enforcement operation successfully disrupted the Lumma Stealer infrastructure, the infostealer operators disabled the IDRAC tool and regained access to the servers.