An SMS Message Could Be Enough to Hack Your Android Phone
- "Over the air" configuration messages can trick recipients into accepting phishing network settings.
- The vulnerable device vendors are Samsung, Huawei, Sony, and LG but two of which have already fixed the issue.
- The attackers don’t need sophisticated equipment to carry out the attack, nor to have much information about the target.
Check Point researchers have identified a vulnerability that underpins a wide range of modern Android devices from Samsung, Huawei, LG, and Sony. According to the report, a malicious actor could send specially crafted SMS messages to the target phone, essentially changing the network settings on the device. These SMS messages are known as “OMA CP” messages, and include network configurations and APN settings that are defined by your mobile network carrier. It’s similar to what you get when you insert a new SIM in a device for the first time.
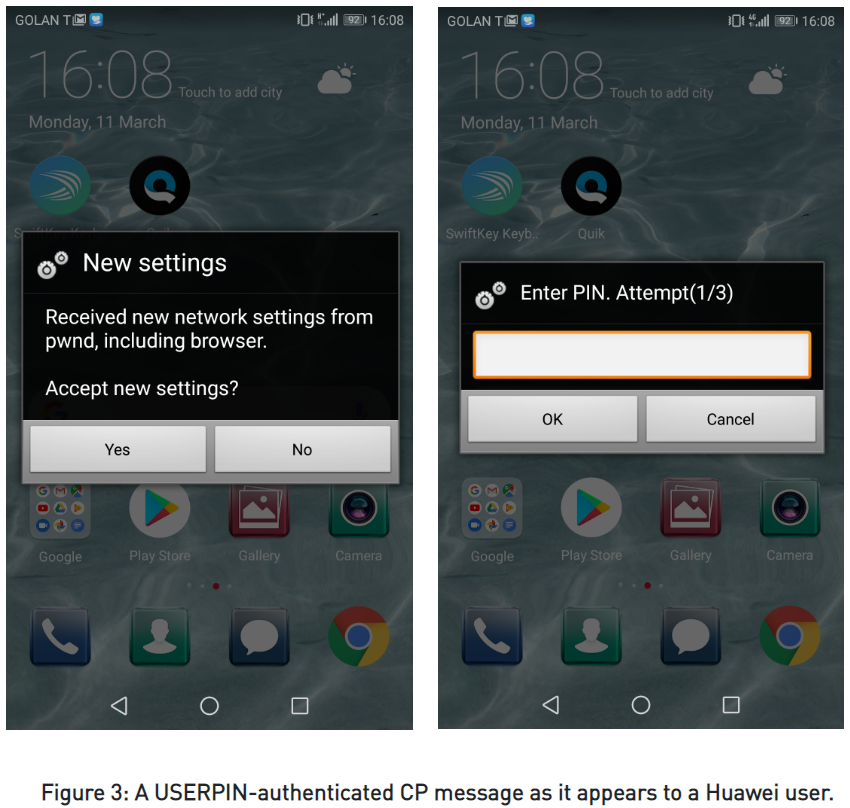
OMA CP messages can change the MMS message server, the proxy address, the browser homepage and bookmarks, the mail server, and the directory servers for synchronizing contacts and calendar data. This makes it possible for an attacker to route all network traffic from a device through a proxy that they control, so all sensitive user data is stolen without the user realizing it at the time. The targets may be tricked by a first SMS that would provide guidance to them, offering a PIN to unlock the new settings, approve, and accept them.
Source: research.checkpoint.com
In other cases, authenticating with a PIN isn’t required, because the attackers may have already gotten their hands to the victim’s IMSI (International Mobile Subscriber Identity). This is a pseudo-confidential 64-bit identifier that is roughly the equivalent to an IP address in computers. For Samsung devices, an attacker wouldn’t need either the IMSI nor a PIN, and the only prerequisite for success is the victim to accept the CP message through the relevant prompt. To launch such an attack, the actors would only need a GSM modem, with cheap USB dongles that can do the job costing a mere $10.
Check Point researchers have tested their proof of concept code on various Samsung Galaxy models, the Huawei P10, LG G6, and the Sony Xperia XZ Premium. As they point out, the susceptibility to the over-the-air attacks works on a wide range of models coming from these four manufacturers, and correspond to about 50% of all smartphones out there right now. The team disclosed their findings to the vendors in March, with Samsung fixing the problem in May, and LG in July. Huawei is planning to plug the flaw by introducing UI fixes for OMA CP in their next generation of Mate and P series devices. Sony did not accept that anything wrong is going on, stating that their devices follow the OMA CP specification and thus, nothing needs fixing.
Have something to comment on the above? Feel free to do it in the comments down below, or on our socials, on Facebook and Twitter.