Merely Viewing a GIF Could Compromise Your Microsoft Teams Account
- Researchers have discovered a way to grab the authentication tokens from Microsoft Teams.
- The exploit chain presupposes the compromise of a Microsoft subdomain and the victim clicking a URL.
- The attacker may also share a malicious GIF file instead, compromising all participants in a meeting.
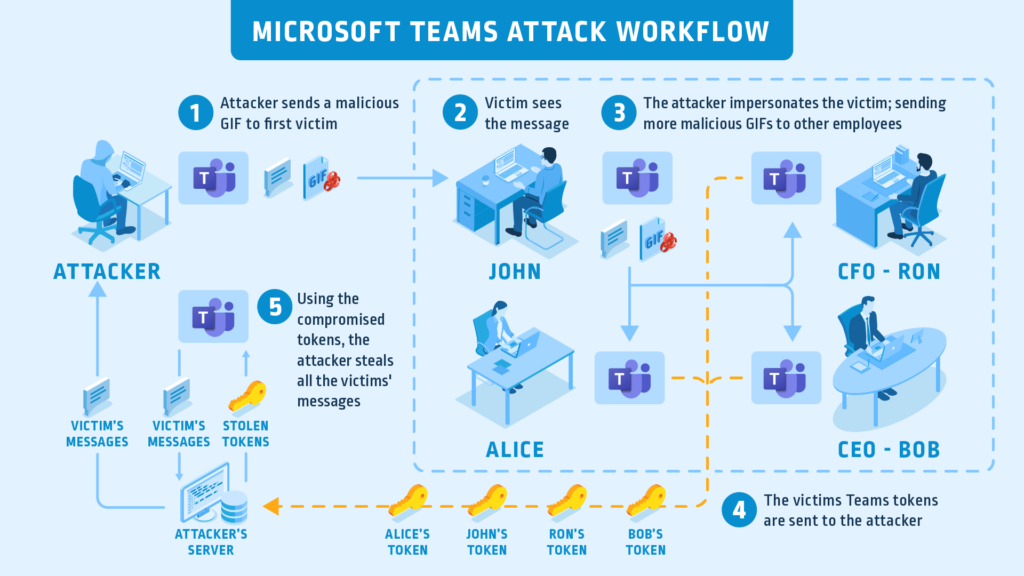
Microsoft has just fixed a pretty nasty vulnerability on Microsoft Teams after CyberArk researchers found a way to exploit it and they shared the details with the company. Teams is a complete workplace collaboration platform featuring video meetings, chat communication, cloud storage, app integration, and more. As such, it is extensively used right now because of the ongoing pandemic, and any flaws in it put thousands of organizations and companies at risk. Unfortunately, the chain of exploitation could be triggered by an effortless action, such as sending a GIF file to the target.
Source: CyberArk
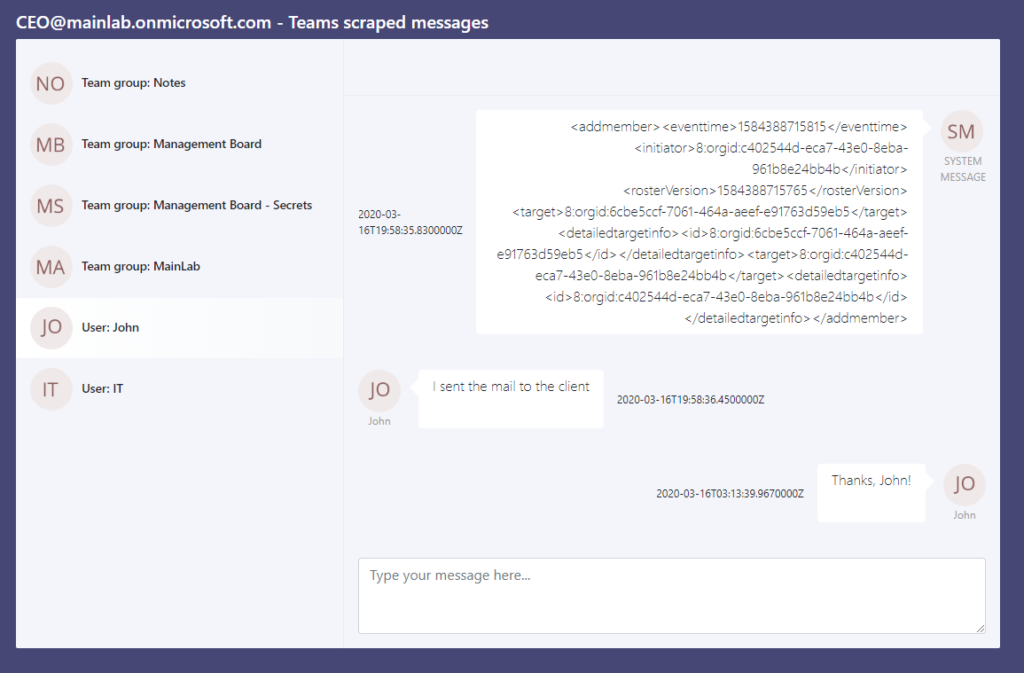
Every time the Teams client is launched, the software automatically generates two access permission tokens that are sent to two subdomains belonging to Microsoft. CyberArk figured that it would be possible for an attacker to take over these subdomains, so the tokens would eventually end up on the server that is controlled by the hacker. This would make it possible for the malicious actor to scrape conversations, or even take over the accounts of all meeting participants. The only prerequisite for this is to work would be to use a valid digital certificate for the compromised subdomain, which is fairly easy to do.
In the following video, CyberArk researchers demonstrate the proof of concept, managing to take over Microsoft Teams accounts.
Apart from what is shown in the above video, the most dangerous scenario of exploitation wouldn’t be the account takeover, but a silent presence on an organization’s Teams platform. It would enable the actors to conduct continuous eavesdropping, explore the various data that is uploaded on the “private” cloud, and traverse freely through the organization’s systems. That said, if a GIF drops on the chat room, don’t click on it without a second thought. Even better, companies could enforce a policy where they could forbid the sharing of URLs and GIF files on their Team chat rooms.
Source: CyberAark
While Microsoft didn’t try to play down the severity of the discovered vulnerability, they stated that nothing bad concerning this flaw had happened yet. The tech firm has secured the subdomains by deleting the misconfigured DNS records, so attackers can’t take them over anymore. A spokesperson stated that there had been no cases of this vulnerability being used in the wild, so it is likely that CyberArk’s team was the first to discover this.