Critical MediaTek Rootkit Was Left Unpatched for Over a Year
- More than a dozen MediaTek 64-bit processors are vulnerable to a critical vulnerability.
- The flaw was known for over a year, and MediaTek had released a fix for it in May 2019.
- Google has finally identified the problem in the latest March 2020 Android Security Bulletin, making widely known.
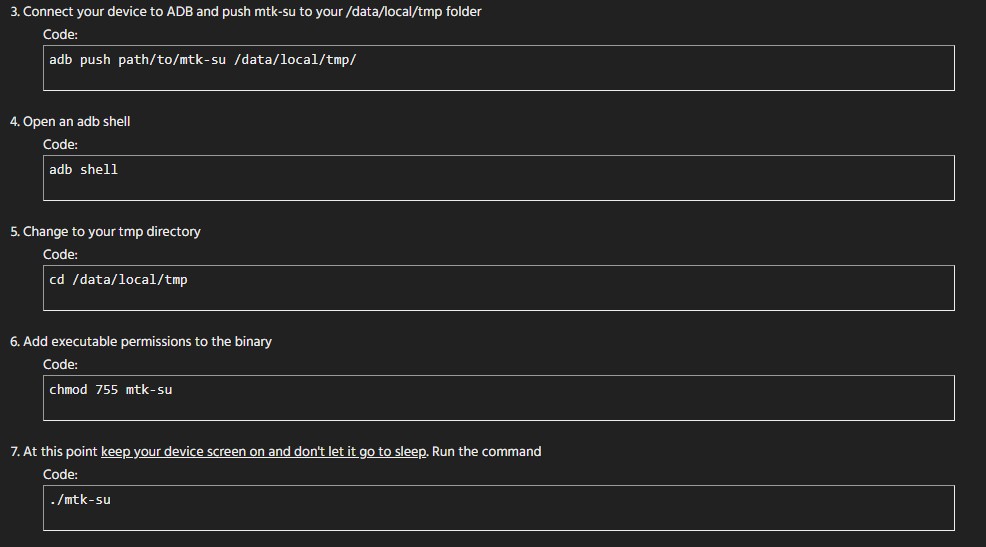
Back in February 2019, a software developer and user of the XDA forums (nickname: “diplomatic”) released a rootkit (MTK-su) which exploited a vulnerability (CVE-2020-0069) in a range of Amazon Fire devices to temporarily gain root access on the tablets. As the flaw was specific to MediaTek processing units, diplomatic kept on updating the rootkit to cover smartphone models of up to Android 9, with the latest release version 20 becoming available in December 2019, adding support for yet another two MediaTek CPUs (MT6580, and MT8183). The author of the rootkit states that the exploit was working on virtually all of MediaTek’s 64-bit chips.
The number of devices affected by this was pretty large, with various models from Alcatel, Amazon, ASUS, Blackview, Huawei, LG, Meizu, Nokia, Motorola, OPPO, Sony, Realme, Xiaomi, and ZTE being vulnerable to the exploit. MediaTek processors are a cost-efficient option for device makers, so almost all phone manufacturers have at least a couple of budget models in their range using them.
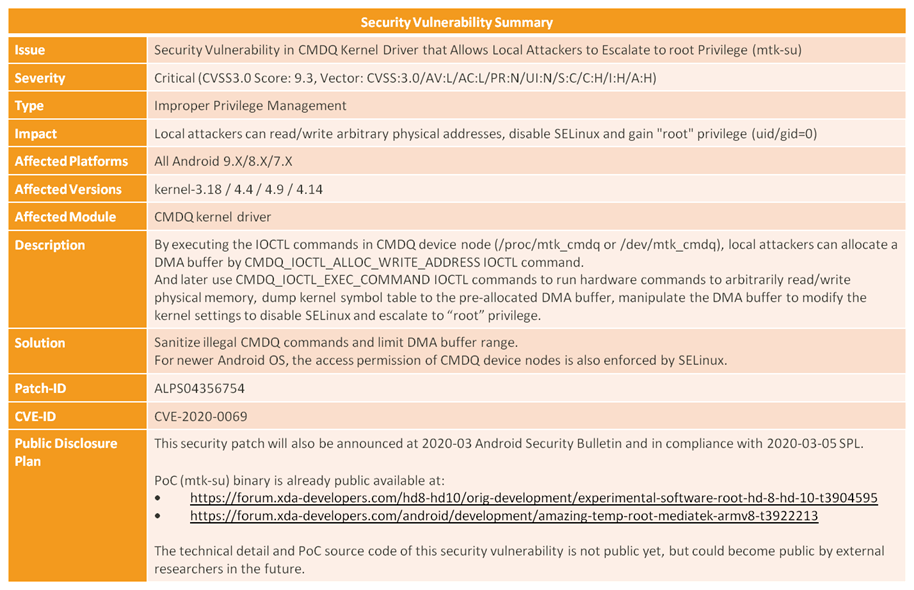
The reason why "MTK-su" has a CVSS v3.0 score of 9.3 is that it is qualitatively different from the usual rooting methods. Instead of relying on the unlocking of the bootloader and the creation of a superuser, MTK-su only needs to copy a script on the device and execute it in a shell. This makes it possible for a malicious app to drop it on the phone without the user realizing, execute it, and gain root access on the device. If an app gains root access to an Android device, no security measures can stop it, since it can grant itself any permission it wants. This means that it can potentially access user files, activate microphones and cameras, and even brick the device.
Source: XDA Forums
MediaTek looked into the rootkit and discovered that it affects devices that run on Linux kernel versions 3.18, 4.4, 4.9, or 4.14 and Android versions 7 Nougat, 8 Oreo, or 9 Pie. This means that MediaTek devices running Android 10 aren’t vulnerable to MTK-su. The Taiwanese chipmaker released a fix in May 2019, but not many of the affected devices have received the fixing patches from their manufacturers. These budget phones are usually not receiving any security updates for long after their release, as the vendors don’t dedicate their valuable developing resources to support these low-cost devices.
Source: XDA Forums
So, time went by, mobile malware authors took advantage of what was on offer at the XDA forums, and Google was simply hoping that no one would notice. This remained the case until the latest Android Security Patch of March 2020, where Google decided to finally address the critical flaw and incorporate MediaTek’s fix. This means that if you have this latest patch, you’re safe. If not, install a mobile security suite to protect yourself from malicious rootkits that may try to execute on your device.