Banking Trojan Database Exposes Financial Details of Millions of Victims
- Two unprotected MongoDB instances were accessible without password and indexed by search engines.
- The databases contained 2.2 million passwords belonging to about 753k people, although there could be duplicates.
- The victims are mainly from Europe, and their personal information has probably reached multiple actors now.
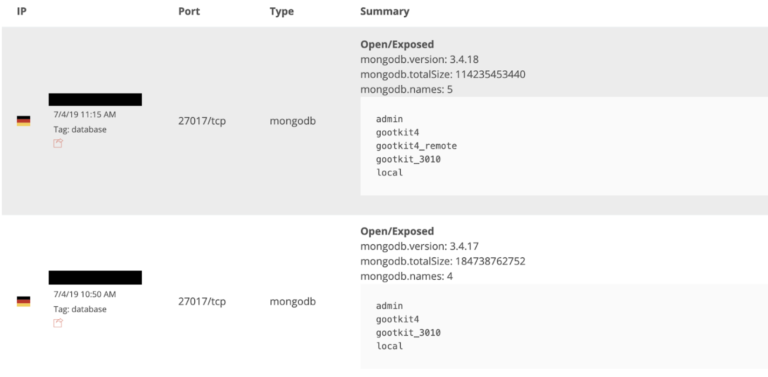
Security researcher Bob Diachenko warns about his most recent findings which include two open and publicly accessible MongoDB instances. Upon more in-depth inspection of the contained data, the researcher figured out that it is actually the exfiltrated information of an operation that was based on the GootKit banking trojan. GootKit is not very popular right now, but it was widely successful back in the summer of 2014. Both MongoDB instances were indexed by public search engines, so this find wasn’t a difficult one for Diachenko or any other person who is actively looking for open databases.
Source: securitydiscovery.com
The databases were taken down on July 10, 2019, so they appear to belong to the same group or person. The actors possessed passwords in plain text form, bank account details, email account login credentials, online shop credentials, and credit card details. In total, the researcher has found 1.44 million email accounts, 2.2 million passwords and configuration pairs, and about 753k usernames. Besides the personal data, the instances also contained malware configuration details that could be interesting for researchers.
Source: securitydiscovery.com
GootKit is still a very intrusive and capable malware tool that is mainly used against Europe-based victims. It looks like the malicious actors who were deploying it were not careful enough to secure the exfiltrated data. Analysis of the leaked information shows that the victims are mainly from Poland, France, the United Kingdom, Italy, and Bulgaria. Whether or not the researcher is planning to somehow help inform the 752 thousand victims that their data was exfiltrated and now leaked further, has not been clarified. We have asked Diechenko about his intentions on that part, and we will update this post as soon as we hear back from him.
Most of the victims must not have realized that GootKit has stolen their sensitive personal data, and since the two instances were indexed by search engines, it is very likely that the data has now been copied by multiple actors. This creates a catastrophic situation for the victims, as they were very little time to react. With more actors holding this information, the exploitation of the victims becomes imminent before the data is rendered useless or less valuable. The funny side of the incident is that the cyber-crooks who failed to secure their database with a password will see their criminal hard work go down the drain.
Update: Bob Diachenko informed us that all of the affected users should have already received a notification email by now. Moreover, he is planning to share the info with Troy Hunt, so a new entry on HaveIBeenPwned will be added soon.
Have something to comment on the above? Feel free to do so in the dedicated section down below, or on our socials, on Facebook and Twitter.